TL;DR
Selecting and evaluating Internal Developer Platforms (IDP) is no longer about picking a tool with the longest feature list; it’s about finding the right fit for your team’s maturity, delivery speed, and governance needs. The best Internal Developer Platforms don’t just automate pipelines; they align with how your teams already build, ship, and secure software.
1. Match Platform Complexity to Team Maturity
Not every team needs an enterprise-grade orchestration system from day one. Smaller startups or teams under 50 developers often see faster ROI from managed or plug-and-play Internal Developer Platforms (IDPs), which can cut setup time by nearly 70% compared to traditional self-hosted options.
For larger organizations managing hundreds of microservices, platforms like Cycloid bring more flexibility. These allow deep customization and connect directly with your existing CI/CD and Infrastructure as Code (IaC) stacks, reducing the need to rebuild what’s already working.
2. Align With Your Existing Toolchain and Cloud Strategy
Compatibility is the easiest way to avoid future friction. Evaluate how well an Internal Developer Platform (IDP) integrates with your CI/CD tools (GitHub Actions, Jenkins) and IaC frameworks (Terraform, Helm, Pulumi). A strong integration can save platform teams 20–30% of maintenance time per release cycle.
Teams with multi-cloud or hybrid infrastructure should prioritize platforms that support unified environment management and abstract away provider-specific configurations. If your delivery model follows GitOps, ensure your IDP supports pull-based automation to prevent drift and improve traceability.
3. Evaluate Governance, Security, and Compliance Needs
Governance should scale with your business, not slow it down. Regulated industries like finance, healthcare, or defense should focus on Internal Developer Platform (IDPs) with built-in audit trails, role-based access control (RBAC), and policy-as-code. Platforms with automated compliance enforcement can reduce policy violations by up to 50%, cutting the manual effort of audits significantly.
For fast-moving SaaS teams, lightweight governance is often enough. An IDP that enables experimentation while keeping minimal guardrails can improve release cadence by 2–3×. The key is balance: choose governance depth that matches your organization’s risk profile.
4. Assess Observability and Cost Accountability
An effective Internal Developer Platform (IDP) should give visibility into who deployed what, where, and at what cost. Platforms offering environment-level cost dashboards typically help companies identify 15–25% of cloud waste within the first quarter of adoption.
For platform teams, it’s about developer engagement where observability goes beyond performance. Built-in dashboards showing deployment frequency, failure rates, and adoption metrics make it easier to measure ROI and demonstrate platform value internally.
5. Plan for Extensibility and Long-Term Fit
The best Internal Developer Platform (IDP) is the one that grows with your stack. Avoid closed ecosystems and look for platforms with open APIs, SDKs, and plugin support that allow future integration without heavy rewrites. Flexibility here can extend platform lifespan by 3–5 years, reducing the cost of future migrations.
Consider how easily the platform adapts to Kubernetes upgrades, new IaC frameworks, or security policies. A sustainable Internal Developer Platform (IDP) should evolve alongside both your infrastructure and your engineering culture, thereby supporting innovation without breaking compliance or stability.
Hands-On Example: Deploying an Application Environment with Cycloid
In this section, we’ll walk through a complete hands-on example of creating a project, setting up environments, attaching a reusable stack, and running a deployment pipeline in Cycloid. This will help you understand how to evaluate Internal Developer Platforms. This practical walkthrough demonstrates how developers and platform engineers collaborate through a single self-service workflow without directly interacting with Terraform.
Step 1: Create a New Project
-
From the Cycloid dashboard, click Projects → Create project.
-
Enter name and description
-
Choose Config Repository: your assigned Git repository
-
Click Create project to initialize.
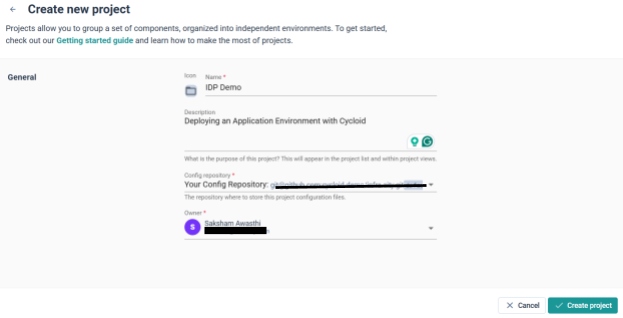
After creation, Cycloid redirects to the project dashboard, where you can manage environments.
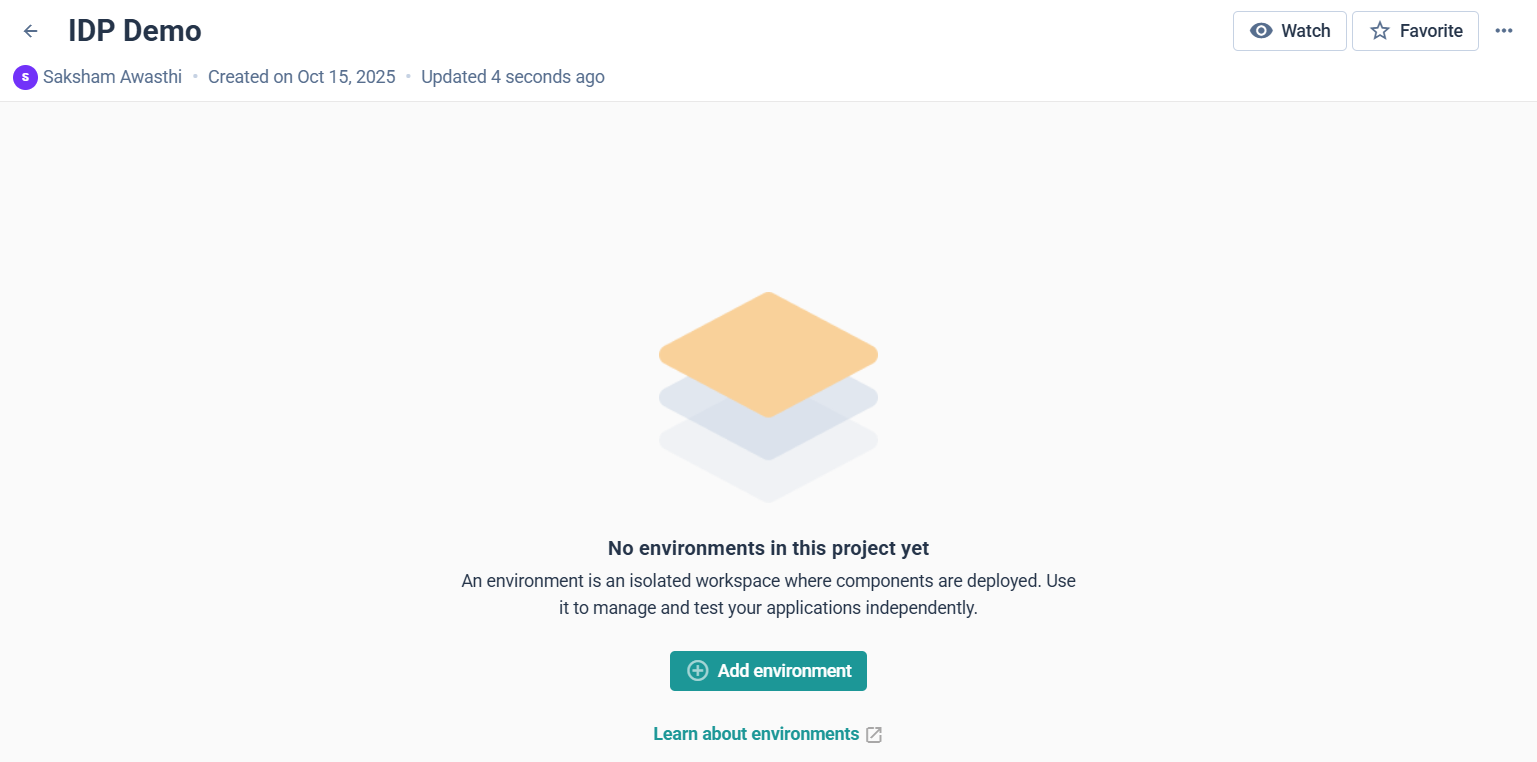
Step 2: Add Environments

- In the New environment dialog, enter a name such as:
dev for development, staging for pre-production, or production for your live setup.

Cycloid automatically groups environments under a single project, each tracked for cost and activity.
Step 3: Create a Component and Choose a Stack
Open the development environment and click Add new → Component.
In the form:
- Component name: frontend
- Description: Deploys the demo web app using Terraform + Kubernetes.
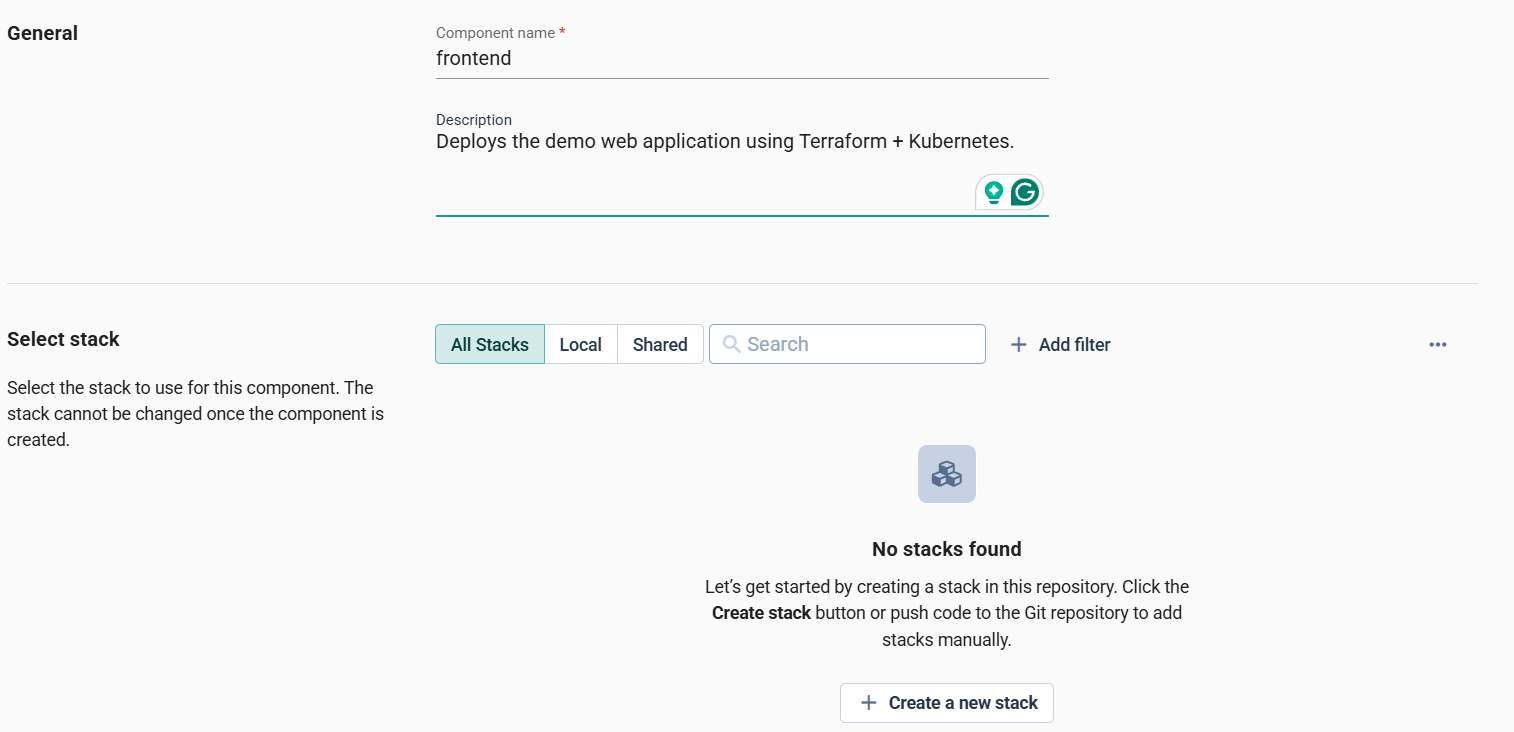
If no stacks are available, click Create a new stack. Cycloid redirects you to the Stacks section.
Select Terraform Blueprint for AWS: this will deploy an EC2 instance using Terraform.
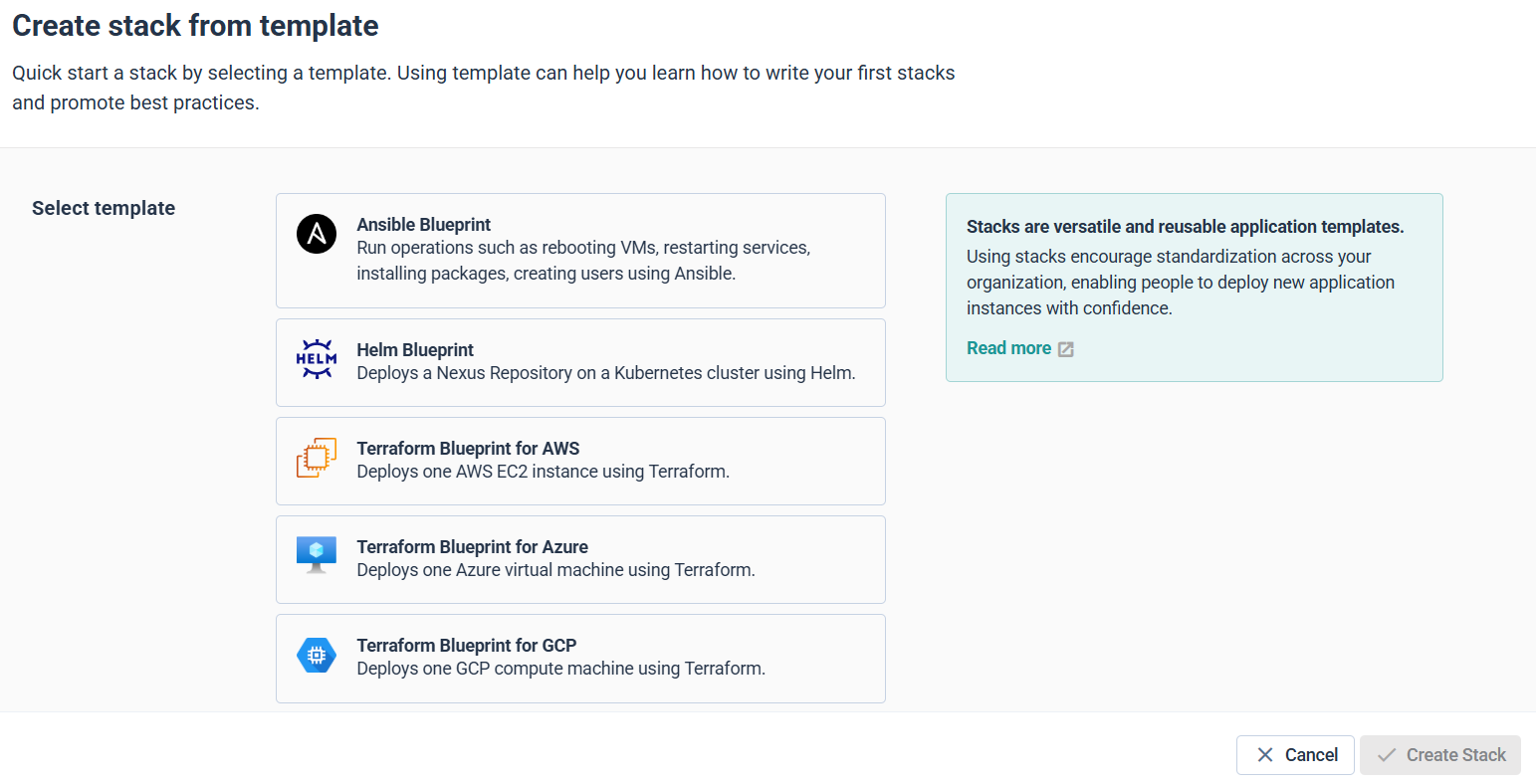 Enter:
Enter:
- Stack name: aws-ec2-demo
- Description: Deploys a single EC2 instance for demonstration.
- Catalog repository: Select your catalog repository from dropdown
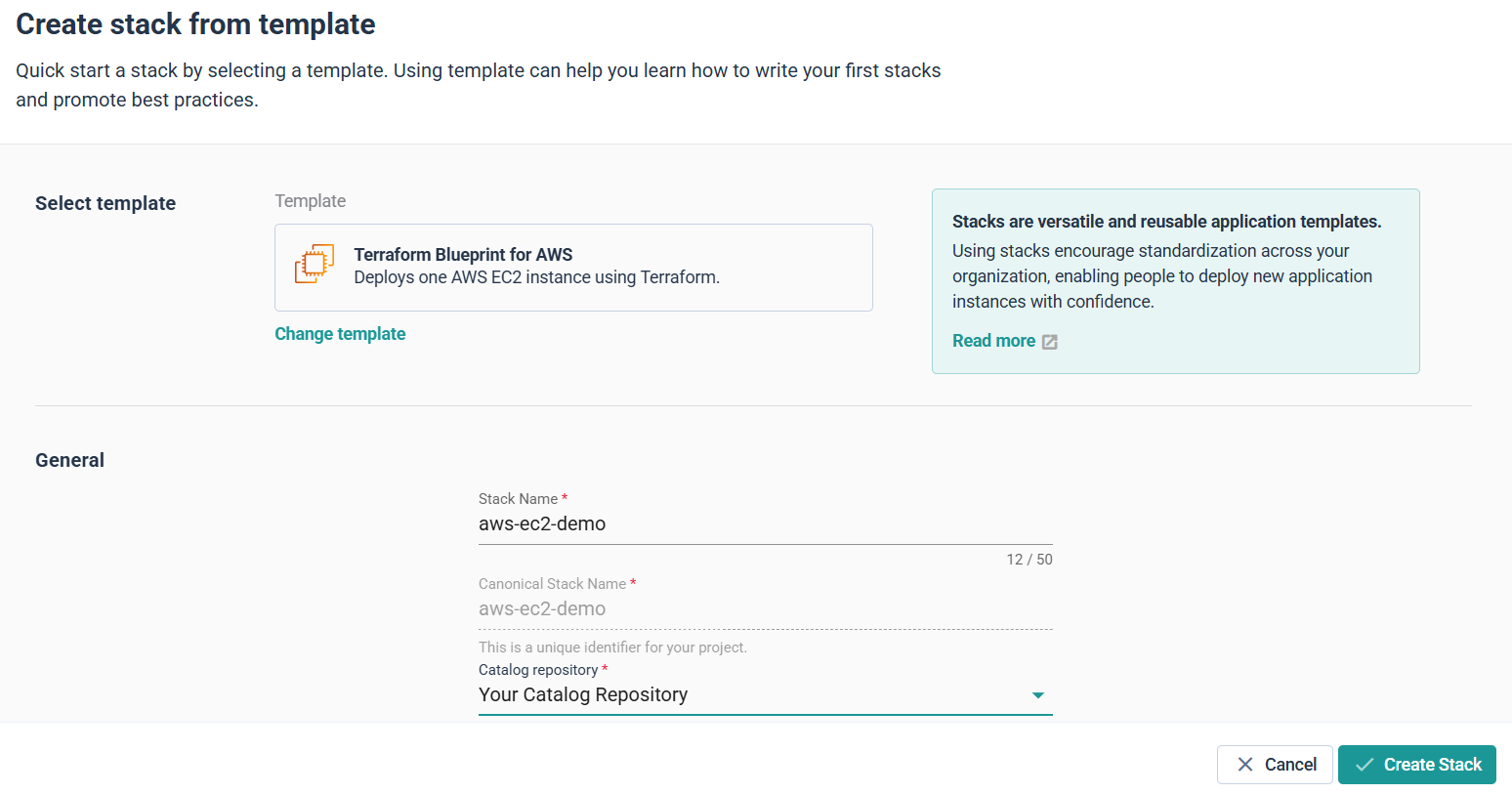 Click Create Stack and return to your environment.
Click Create Stack and return to your environment.
Now reopen the Add component form and link your stack.

Step 4: Configure the Stack and Estimate Cost
After linking the stack, Cycloid opens a configuration screen.
Fill in the required fields:
- AWS Account: select your linked credential
- AWS Region: eu-west-1 (Ireland) or whichever region your account supports.
- Instance type: t3a.small (small enough for sandbox use and cost-friendly)
- Disk size: 20 GB as a baseline. You can increase it if you plan to host larger workloads.
Cycloid integrates TerraCost to estimate cloud spend in real time.
Click Estimate cost to preview monthly cost before deploying.
Finally, click Add component.
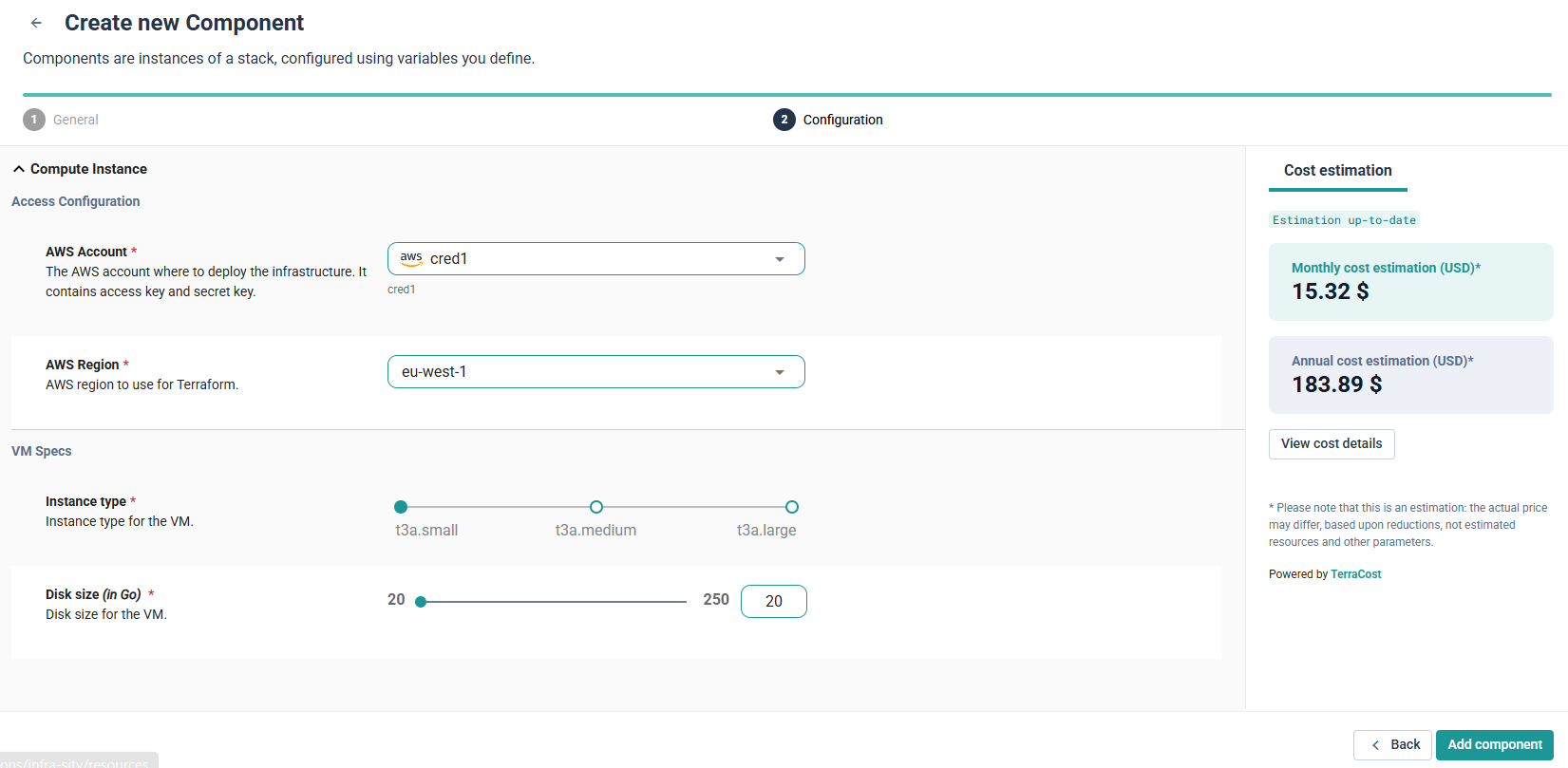
Cycloid’s form-driven provisioning hides Terraform complexity while surfacing cost insights through TerraCost.
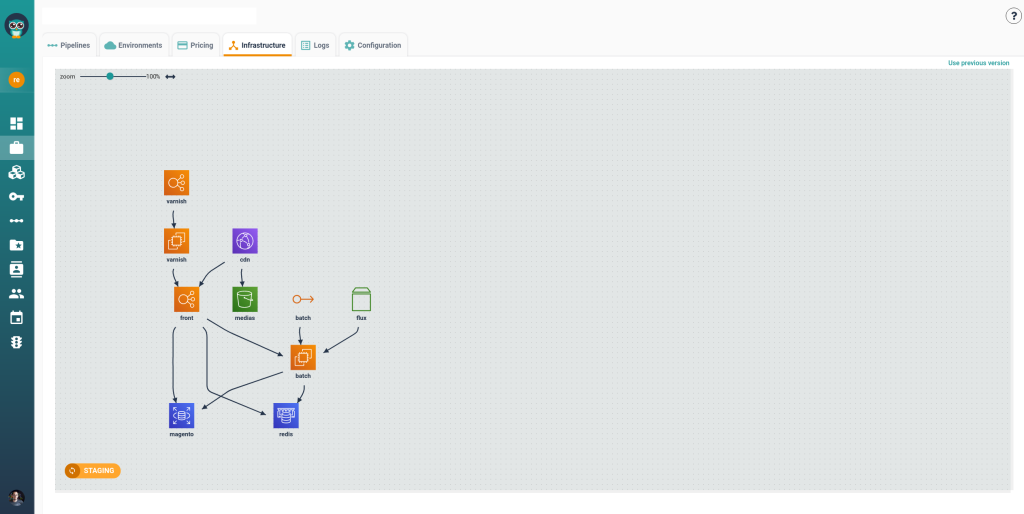
Step 5: Verify Deployment and Monitor Activity
Once deployment starts, Cycloid visualizes the full pipeline automatically.
The view shows:
- git_stack-terraform: Terraform IaC repository
- git_config-terraform: Configuration parameters
- deploy: Terraform plan and apply
- tfstate: Terraform state management
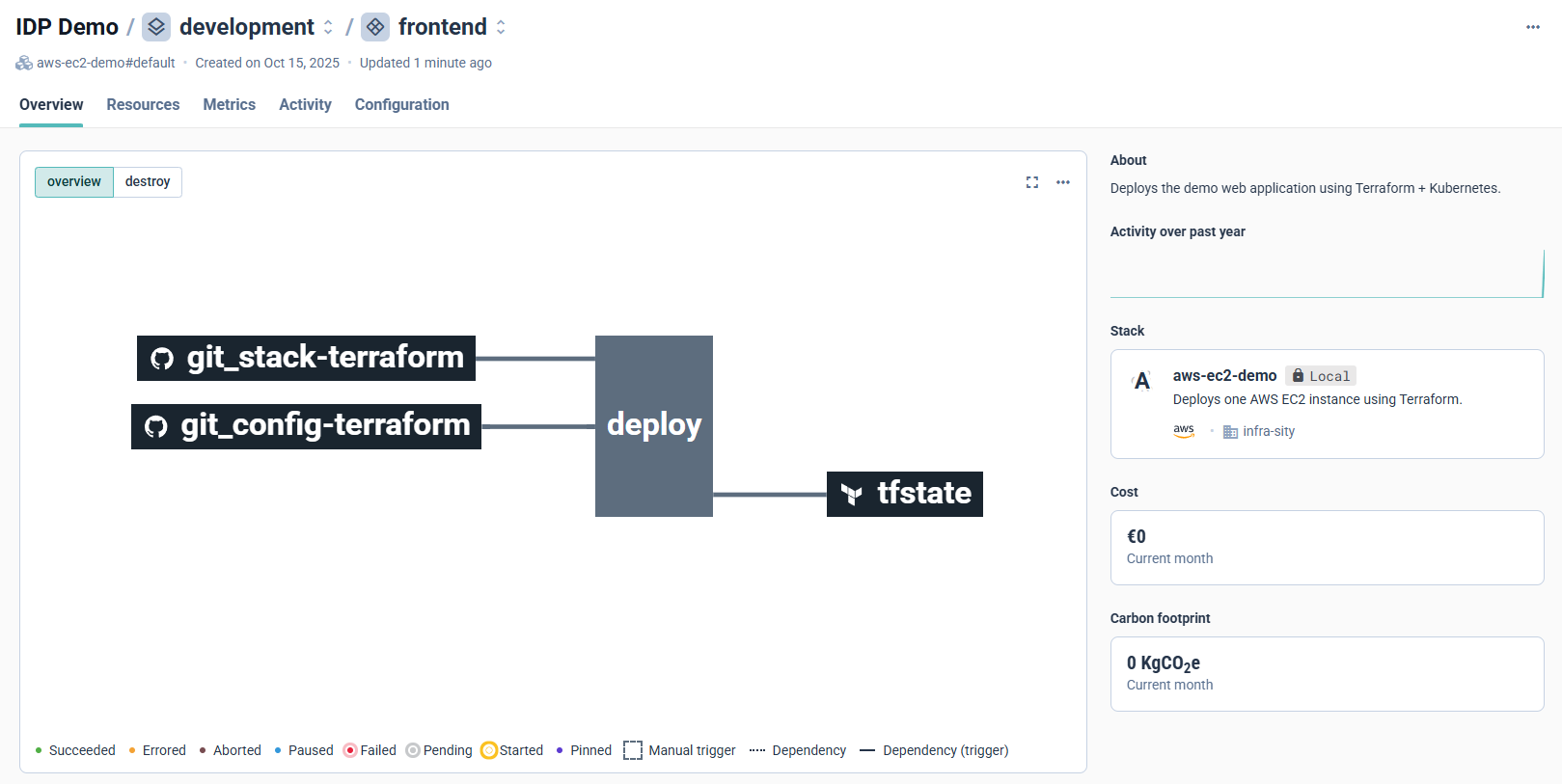
Cycloid visualizes Terraform orchestration from source to state, keeping each step transparent.
In our demo, the pipeline halted at the Terraform apply phase due to IAM restrictions. The log revealed missing permissions (ec2:DescribeImages) for the AWS user.
Instead of hiding such errors, Cycloid exposes them in real time, helping teams pinpoint credential and policy issues without leaving the platform.
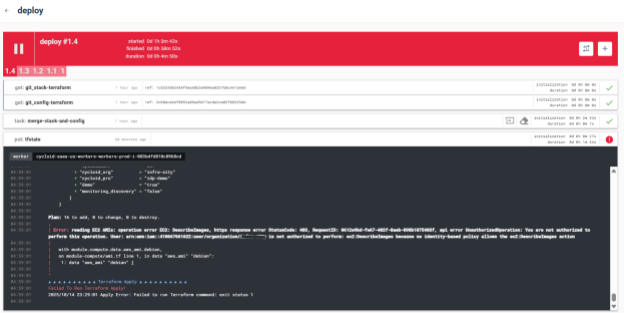
Detailed Terraform logs displayed directly inside Cycloid, surfacing IAM permission issues for immediate troubleshooting.
This scenario actually highlights how Cycloid enforces governance: deployments with insufficient permissions are stopped before any unauthorized resources are created.
Step 6: Clean Up the Environment
From the same dashboard, click Destroy next to overview.
Cycloid safely executes a teardown pipeline that removes any planned or partially created resources, ensuring environments remain clean and compliant.
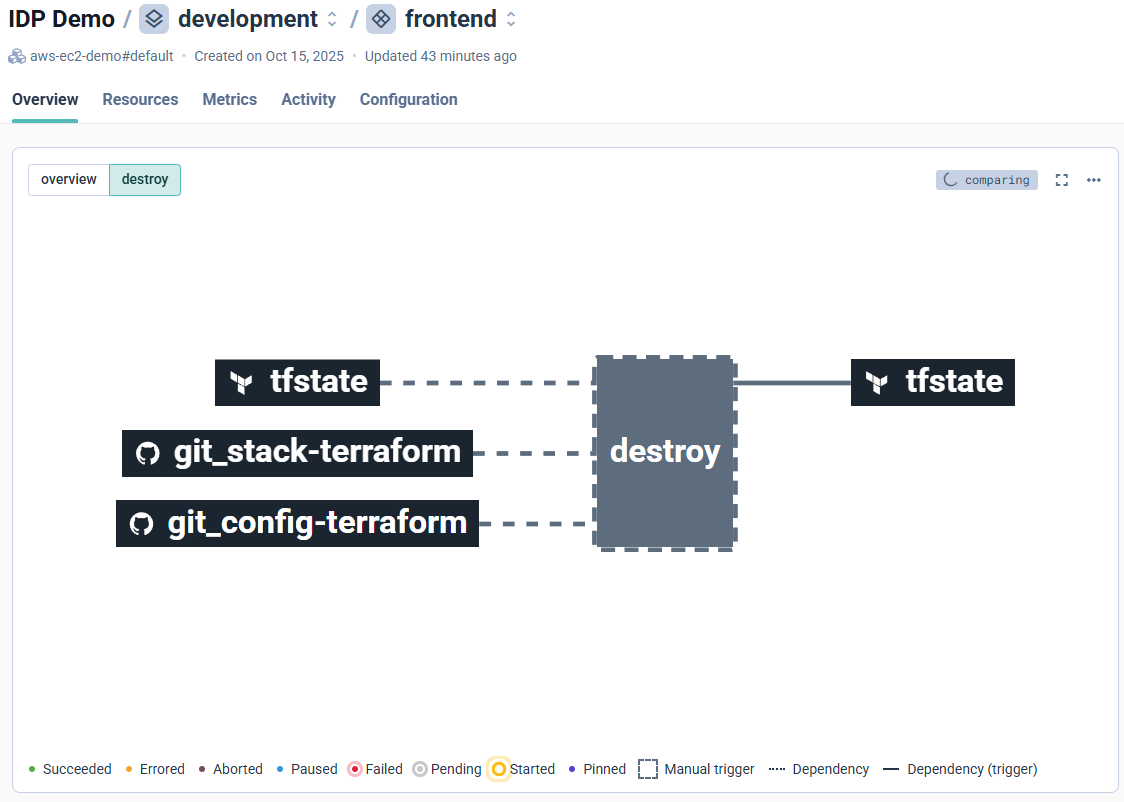
Cycloid provides one-click cleanup to deprovision resources safely and prevent orphaned infrastructure.
Even though our Terraform execution was halted for governance reasons, the destroy workflow demonstrates how Cycloid maintains full lifecycle control: from creation to decommissioning.
What We Achieved in This Walkthrough
In this walkthrough, we set up a project, added multiple environments, attached a reusable Terraform stack, and triggered an automated deployment pipeline; all within Cycloid’s visual orchestration layer.
The failed Terraform apply wasn’t a setback; it was a demonstration of built-in governance. Cycloid surfaced IAM restrictions clearly, prevented unauthorized resource creation, and provided full traceability across the deployment chain.
This exercise shows how teams can use Cycloid not just for automation, but for visibility, accountability, and compliance across every stage of the delivery process.
Key Takeaways
- Self-service without risk: Cycloid lets developers create, deploy, and clean up environments independently, while built-in policies and permissions keep deployments secure and auditable.
- Governance made visible: Even when Terraform fails due to missing permissions, Cycloid’s pipeline transparency ensures that every step, from configuration to failure, is logged, traceable, and actionable.
- Infrastructure clarity in one place: From cost estimates (TerraCost) to live pipeline visualization, every operational detail is surfaced in the same interface, reducing the cognitive load on both developers and platform teams.
- Full lifecycle control: Projects, environments, and components follow a complete lifecycle: creation, deployment, monitoring, and safe teardown, demonstrating how Cycloid unifies DevOps, FinOps, and governance into a single workflow.
Conclusion
Internal Developer Platforms (IDPs) have become a foundation for modern engineering, bringing structure and visibility to how teams build and deliver software. They create alignment between development, operations, and governance, helping organizations maintain speed without losing control. By acting as a single coordination layer, IDPs ensure that what reaches production is consistent, secure, and cost-aware.
Throughout this article, we explored the elements that make an IDP effective, from orchestration, automation, and governance to data sovereignty and flexible hosting models. We looked at how leading platforms approach these challenges differently, and why the right choice depends on a team’s size, complexity, and existing toolchain. The comparisons, features, and evaluation framework together illustrate what defines a mature platform and what outcomes teams can realistically expect. We also walked through a real Cycloid implementation to see these principles in action, demonstrating how projects, environments, and stacks come together through a self-service pipeline.
The role of the IDP is now about bringing clarity to complexity. It helps organizations turn fragmented tools into a cohesive delivery system where developers work with confidence and leaders gain measurable visibility. As teams continue to seek balance between autonomy and governance, the IDP stands as the bridge, keeping delivery fast, secure, and accountable.
FAQs
1. What is the difference between an IDP and a PaaS?
A Platform-as-a-Service (PaaS) offers a managed environment for deploying applications but limits customization and control. An Internal Developer Platform (IDP) is built to orchestrate your own tools (CI/CD, IaC, and governance), giving teams full control over how they deploy, govern, and monitor software while maintaining a PaaS-like experience for developers.
2. Can an IDP replace existing CI/CD tools?
No. An IDP complements your current CI/CD setup instead of replacing it. It connects tools like Jenkins, GitHub Actions, and Terraform into one orchestrated system, making delivery pipelines, infrastructure, and compliance work together seamlessly.
3. Is it safe to let developers self-service production systems?
Yes, when proper controls are applied. Modern IDPs use role-based access, approvals, and policy-as-code to enforce guardrails. Developers gain autonomy, but deployments still follow organizational security and compliance standards.
4. How do I measure success or ROI from adopting an IDP?
Success can be measured through quantifiable metrics such as deployment frequency, lead time for changes, and mean-time-to-recovery (MTTR). Organizations typically see 2–3× faster releases and 20–30% lower cloud costs within the first year, along with higher developer satisfaction and stronger governance visibility.
5. Is building your own IDP a good idea, or should you adopt an existing one?
Building an IDP offers full customization but demands long-term maintenance and dedicated engineering resources. Adopting an existing platform like Cycloid that provides faster rollout, enterprise-grade reliability, and continued feature evolution. Most teams benefit from starting with a proven platform, then customizing as their needs mature.