TL;DR
- Cloud cost management has shifted from a finance-only function to a shared engineering responsibility. The 2025 FinOps Foundation report highlights that 82 percent of enterprises cite cloud waste as a critical blocker, making cost awareness as essential as observability and security in modern delivery workflows.
- Finance-owned dashboards fail developers because they deliver cost data too late, out of context, and in places engineers never look. By the time a finance report arrives, infrastructure is already deployed, bills are locked in, and developers have no opportunity to adjust.
- What developers actually need is real-time visibility embedded in their daily workflows. Cost signals should appear in pull requests, CI/CD pipelines, and dashboards they already use, providing actionable context alongside code and infrastructure changes.
- Without this, cost surprises accumulate: idle test environments running for weeks, oversized databases provisioned “just in case,” or resources deployed outside policy that trigger compliance fines. These are avoidable if cost awareness is shifted left.
- Tools like Cycloid make this shift possible by embedding cost checks into developer workflows, showing diffs in pull requests, enforcing guardrails in pipelines, and providing branch-scoped environments that automatically tear down. Costs become visible and actionable before deployment, reducing waste without slowing teams down.
- FinOps maturity is a cultural as well as technical journey. The most effective path is incremental: start with spend baselining, enforce tagging, add pre-merge cost estimation, then introduce ephemeral environments and progressive enforcement. Done right, FinOps becomes invisible until actionable, empowering developers to make financially sound decisions at speed.
Introduction
Cloud bills have grown into one of the most unpredictable challenges for engineering teams. Despite careful planning, most organizations overshoot their budgets, often discovering the damage only after monthly invoices arrive. According to the 2025 FinOps Foundation State of FinOps Report, 82 percent of enterprises reported that cloud waste has become a critical blocker to scaling efficiently. This shift means cost visibility is no longer just a financial concern; it now sits alongside observability and security as a first-class engineering requirement.
In a recent thread on Reddit’s r/devops, engineers lament that while finance teams build beautiful dashboards, developers rarely see cost data in their daily workflows. One comment reads: “If it doesn’t show up where devs work, it might as well not exist.” This complaint and others echo what Cycloid’s documentation emphasizes: cost feedback needs to be embedded into CI/CD pipelines, pull requests, and dashboards so that developers can act on cost implications early.
This is precisely where Cycloid steps in. Unlike FinOps point solutions that provide retrospective analysis after deployment, Cycloid’s orchestration layer embeds cost awareness directly into the development and delivery workflow. In this blog, we’ll explore why finance-only dashboards fall short for developers and why cloud cost awareness must be treated as a first-class signal in engineering workflows. We’ll outline what developers actually need, real-time visibility, actionable context, and cost checks embedded in CI/CD pipelines, while also highlighting the kinds of surprises that emerge without this shift, from idle test environments to oversized databases and even compliance-related fines. Finally, we’ll examine how Cycloid enables this proactive model by surfacing estimates in pull requests, enforcing guardrails in pipelines, and providing practical steps such as ephemeral environments and progressive enforcement to make FinOps part of everyday development.
Current Landscape and Gaps
Most teams already use some form of tooling to keep cloud bills in check. Infrastructure engineers reach for Infracost to estimate Terraform changes before deployment, Kubecost to monitor Kubernetes workloads in real time, or CloudZero to map cloud spend to products and business units. These tools do their job well, but they are typically siloed, retrospective, or finance-oriented. In practice, this means costs are analyzed after infrastructure is provisioned, or in dashboards that rarely reach developers.
The gap is very clear; developers don’t get actionable cost visibility where they work. A Terraform plan might be estimated in a separate tool, but the results don’t automatically flow into a pull request review. A Kubernetes cluster may have Kubecost hooked up, but that insight doesn’t prevent a developer from creating an oversized workload in the first place. Finance platforms can map costs ideally, but by the time the numbers land in their reports, the money has already been spent.
This creates tension between speed and financial responsibility. Startups deploying dozens of times per day risk runaway spend from idle test environments or forgotten resources. Enterprises in regulated industries struggle with enforcing cost and compliance guardrails without slowing down delivery. In both cases, the lack of real-time, developer-first visibility means cost overruns are discovered too late, when infrastructure is already running and budgets are already blown.
What is FinOps and Why Developers Should Care
FinOps, short for Financial Operations, is the practice of bringing engineering, finance, and operations together to manage cloud costs more effectively. At its core, FinOps rests on three principles: visibility, accountability, and optimization.
- Visibility is more than monthly billing dashboards. It means developers can see the projected financial impact of infrastructure changes as they code. For example, a pull request that adds a new database instance should include an estimated monthly cost difference, the same way tests show pass/fail. This lets engineers make informed choices before resources are provisioned.
- Accountability is about shifting financial responsibility upstream. Instead of finance teams raising red flags weeks later, pipelines can enforce cost guardrails in real time. A deployment that exceeds a budget threshold might trigger a warning or block until reviewed, tying technical actions directly to financial outcomes.
- Optimization is the ongoing practice of making infrastructure leaner and smarter. That could mean automatically tearing down ephemeral test environments, enforcing tagging to track spend by team, or right-sizing instances so they scale with demand rather than sitting idle at peak capacity.
These principles apply differently depending on the organization. In startups, visibility and optimization mean preventing waste before it happens, catching idle environments and oversized resources before they hit production. In enterprises, accountability is crucial, because budgets must stay predictable and compliance rules must be enforced at scale. In both contexts, FinOps ensures developers treat cost as another quality dimension, alongside performance and security, rather than an afterthought discovered at the end of the month.
Infracost (Terraform cost estimation)
Developers often start with Infracost to estimate infrastructure costs before deploying. The workflow plugs into Terraform plans:
| terraform plan -out=tfplan terraform show -json tfplan > plan.json infracost breakdown –path plan.json |
This outputs projected monthly costs for new or modified resources. The challenge is that unless this step is wired into pull requests, the numbers remain separate from the review process. Developers see the estimate in the terminal, but not in GitHub or GitLab where the merge decision is made.
Kubecost (Kubernetes cost monitoring)
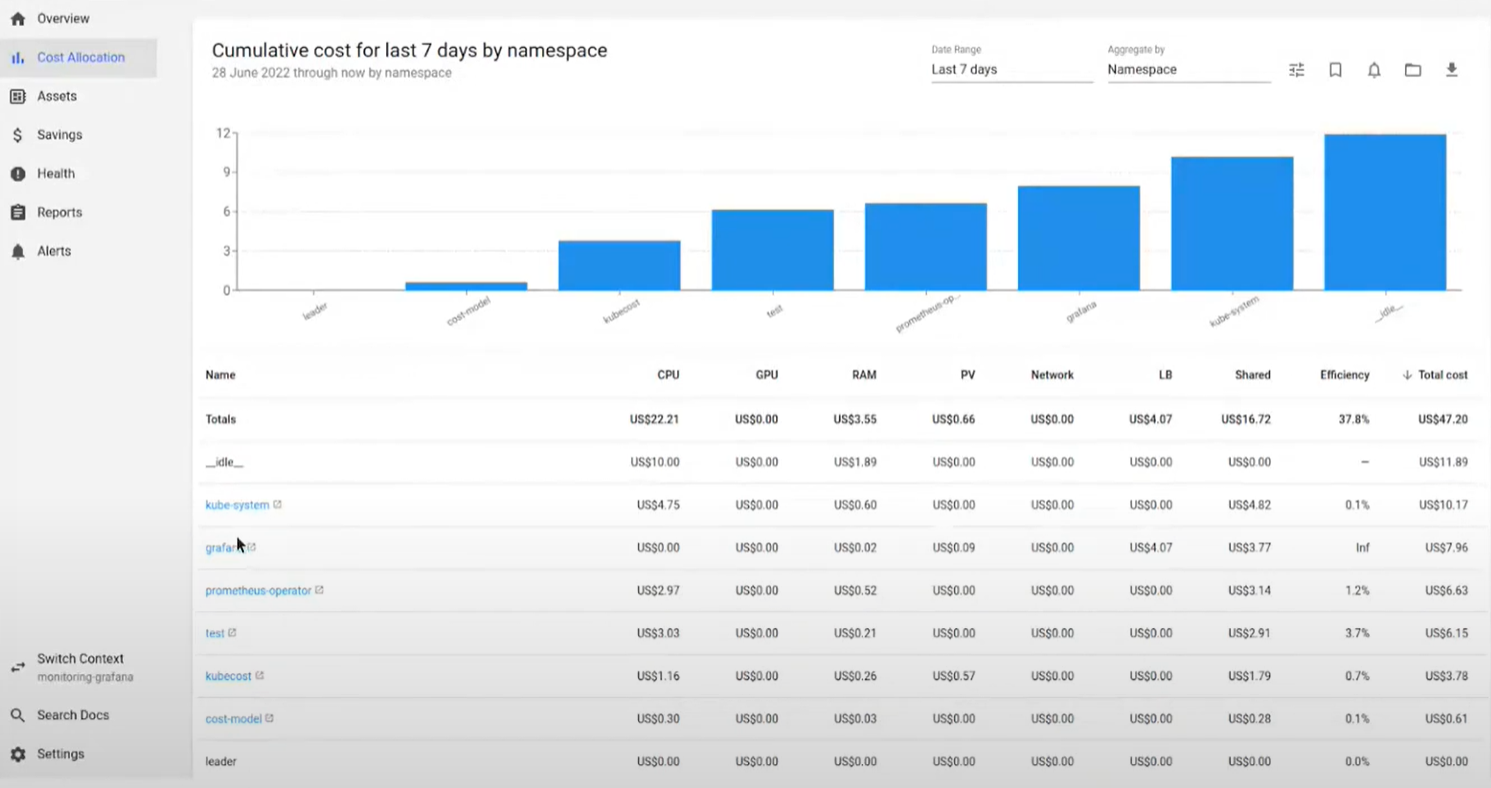
For teams running Kubernetes, Kubecost is often the first tool they reach for. Once installed into a cluster, it collects usage data and breaks it down by namespace, workload, or label. The screenshot below shows a seven-day cost allocation by namespace, with CPU, RAM, and storage usage rolled up into total spend.
This makes it easy to see where money is going inside a cluster, for example, spotting whether the test namespace or a monitoring stack like prometheus-operator is consuming more than expected. It’s especially helpful for surfacing “idle” costs that accumulate quietly.
The limitation, though, is that Kubecost reacts to workloads already running. Developers get visibility into which pods or namespaces are expensive, but they don’t get proactive warnings when provisioning an oversized node pool or spinning up resources outside policy. In other words, the cost signals arrive after the fact.
Why Orchestration Is Needed
The challenge isn’t that teams lack tools; it’s that cost awareness remains fragmented and reactive. Infracost works at the Terraform level, Kubecost tracks Kubernetes, and CloudZero maps business spend, but none of these connect cost signals directly to developer workflows. Developers need a single orchestration layer that embeds financial visibility into the same places they already check for tests, linting, or security scans. Without it, cost awareness stays scattered across dashboards and tools, rather than guiding decisions in real time.
Cycloid: Embedding FinOps into Developer Workflows
This is where Cycloid comes in. Instead of leaving cost awareness in separate dashboards or retrospective reports, Cycloid embeds it directly into the development and delivery workflow. Cost estimates appear alongside code diffs in pull requests, guardrails are enforced automatically within CI/CD pipelines, and ephemeral environments tie spend to specific branches. By shifting FinOps left, Cycloid ensures developers see the financial impact of their work before it turns into expensive mistakes, making cost as much a part of daily engineering as tests or security checks.
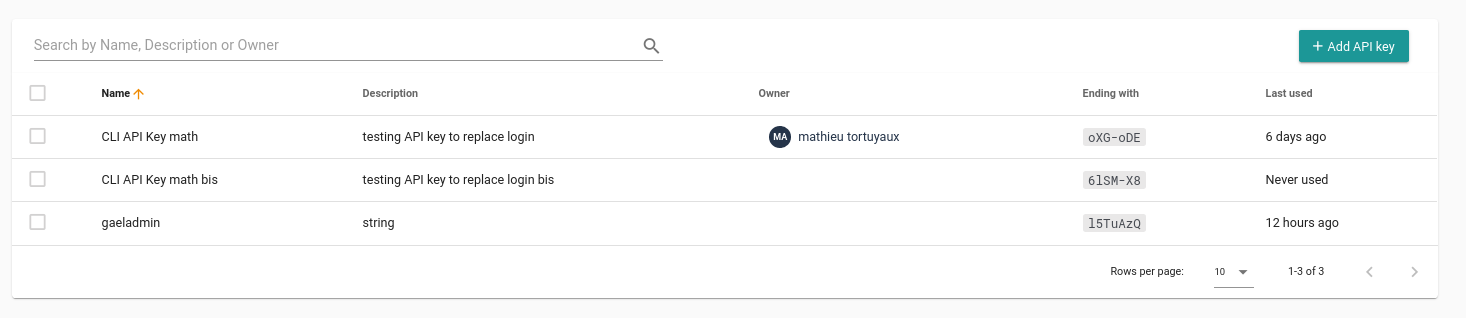
The above image is of Cycloid’s API keys list, which illustrates how developers securely connect cost estimation and policy services into their pipelines. The principle of accountability becomes concrete here: each API key ties specific engineering actions (like PR checks or pipeline runs) to measurable cost outputs, making FinOps part of day-to-day development tasks.
A common misconception is that FinOps belongs solely to finance teams. In reality, leaving cost ownership to finance means problems are caught too late, when infrastructure is already deployed and spending is locked in. Cycloid’s orchestration layer changes this dynamic by giving developers the same level of cost insight and control they have for performance or security. Dashboards, APIs, and policy enforcement make cost a shared responsibility, shifting it left in the delivery lifecycle. By doing so, Cycloid ensures that cost considerations become part of the developer experience, not a surprise buried in a billing report.
Real-World Use Cases of Developer-Centric FinOps
Continuous Delivery Teams and SaaS Startups
For SaaS companies, speed is everything. Teams using Vercel or Netlify-style pipelines often deploy dozens of times a day, sometimes more. That pace, while great for customer value, comes with a hidden cost: the cloud bill scales just as fast as the features being shipped. Traditional FinOps tools only surface those costs after infrastructure is deployed, which is often too late to take meaningful action.
Cycloid changes this by exposing projected spend during the development cycle. With the Cycloid Cost Estimation API, developers see the financial impact of their infrastructure changes before a merge happens. A pull request is no longer just a technical diff; it includes a cost diff as well. If a new service doubles compute spend, developers know immediately and can adjust before it ever hits production.
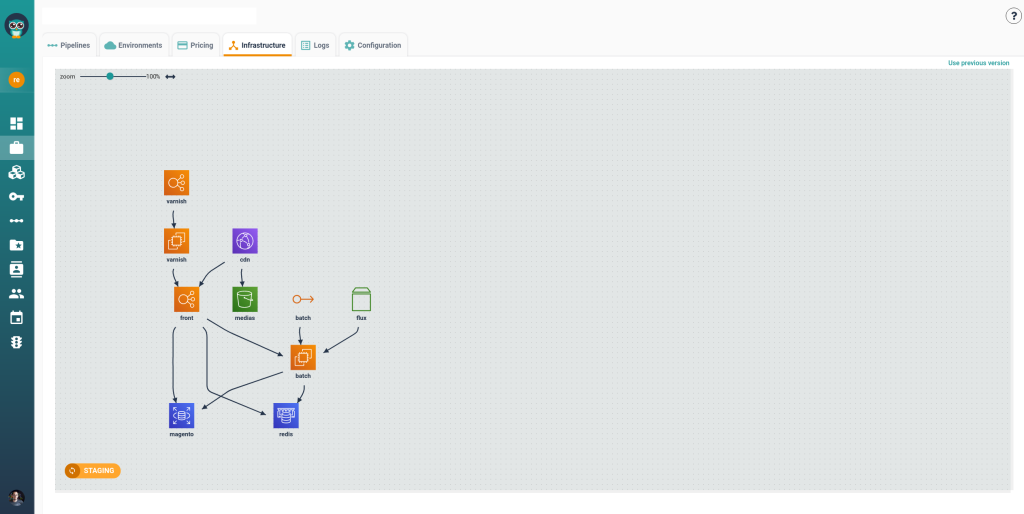
This branch management view shows how Cycloid connects infrastructure environments directly to Git branches. For SaaS teams deploying 20+ times a day, each feature branch spins up its own environment, tracked with cost metadata. When merged, the environment is destroyed automatically. The image reinforces how short-lived branches not only prevent merge conflicts but also eliminate hidden cost creep from idle infra.
Cost is further reduced through Cycloid’s environments as code. In practice, this means that ephemeral environments spin up when needed, tied to feature branches, and automatically shut down when no longer in use. Coupled with feature flag systems, this approach avoids idle infrastructure and keeps test environments from bloating into hidden cost centres. For high-productivity SaaS teams, embedding FinOps this way makes cloud efficiency a natural part of daily delivery, not an afterthought.
Enterprise and Regulated Industries
The challenges look different in large enterprises and regulated sectors such as banking or healthcare. Here, compliance and predictability are just as important as cost control. A surprise spike in cloud usage isn’t just expensive; it can trigger regulatory scrutiny and operational risks.
To address this, enterprises turn to policy-driven guardrails. Cycloid addresses this with its policy engine, which enforces guardrails across accounts and environments. Instead of waiting for finance to highlight overspend after the fact, policies prevent non-compliant or over-budget resources from ever being provisioned. A team attempting to spin up oversized instances outside of defined rules will see the deployment blocked or flagged before it reaches production.
The OPA engine has a dedicated command for testing. The best practices suggested in the OPA testing documentation should be followed. Other than the opa test command, the OPA ecosystem has a Playground that can be used for fast and simple assertions.
To validate your Terraform Plan against the defined policies, you can use the Cycloid pipeline
In a pipeline context, a Concourse Resource is available and can be easily plugged right after a terraform plan step and just before a notification mechanism.
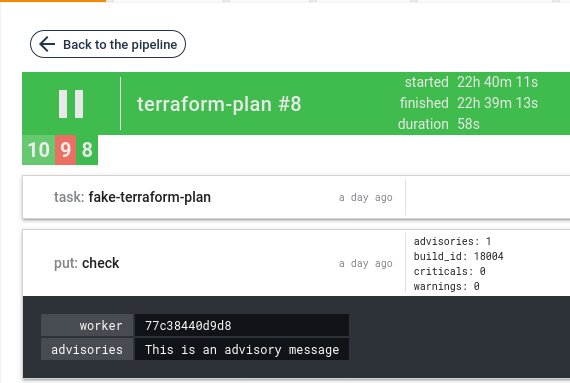
Example of output
Validation with advisories, the job is green and display advisories result as metadata:
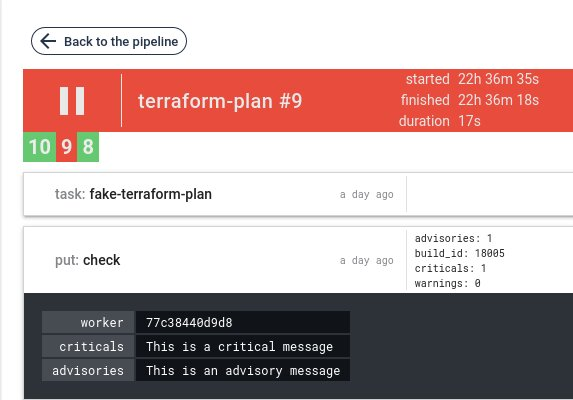
Validation with criticals and/or warnings, the job fails and display result as metadata:
Quality assurance and approval processes also tie directly into Cycloid pipelines. Cost checks become part of the same workflow that governs security scans and test validations. This means deployments cannot bypass review stages without meeting both compliance and cost requirements. For enterprises, this proactive orchestration ensures that cloud bills remain predictable, regulatory standards are met, and no uncontrolled spend slips through hidden in complex environments.
Embedding FinOps into CI/CD Workflows
One of the strongest levers for embedding FinOps into developer experience is the CI/CD pipeline. This is where code becomes infrastructure, and it is also the point at which costs can either spiral out of control or be proactively managed. Traditional point solutions step in only after the deployment is complete, analyzing the bill when it arrives. Cycloid takes a different path by making cost checks an integral part of the delivery pipeline itself, ensuring that engineers get immediate feedback as part of their daily workflow.
Pre-Commit and Pre-Merge Cost Checks
A typical developer flow might begin with a simple git push. With Cycloid integrated into the pipeline, this action not only triggers unit tests and linting but also runs a Terraform integration with Infracost to calculate projected costs for any infrastructure-as-code changes. The results are surfaced directly in the pull request, alongside code diffs.

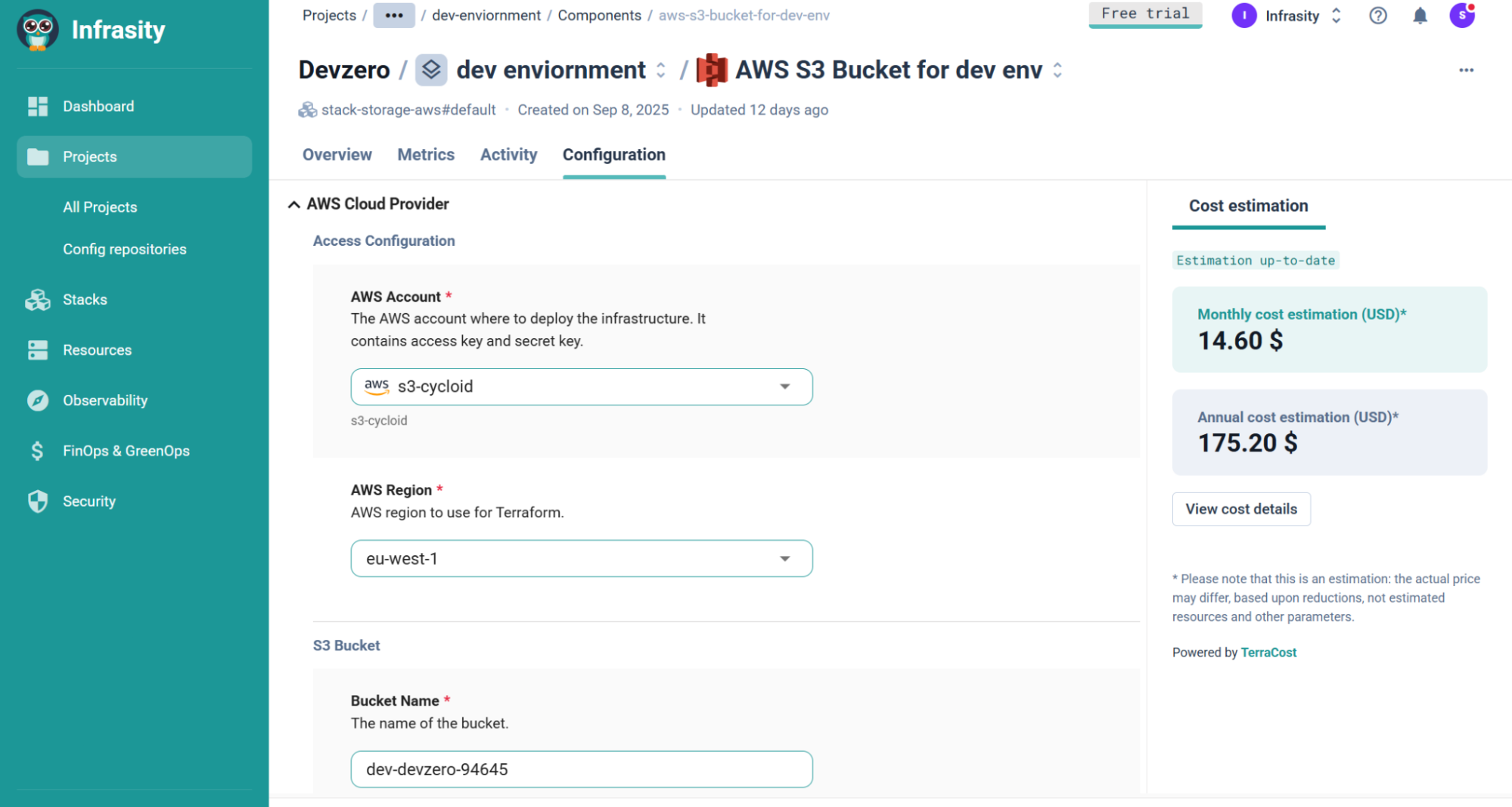
This step-by-step AWS credential in Cycloid illustrates how cost awareness is injected into the CI/CD pipeline itself. Once credentials are integrated, Cycloid can run Terraform plans and Infracost estimates automatically. For developers, the cost diff becomes just another check in the PR status, alongside linting and tests, reinforcing the “invisible until actionable” model.
For developers, this means every commit carries not only functional implications but also financial visibility. A PR that would add a new Kubernetes node pool or scale a managed database will include the estimated monthly cost before merge approval. With Cycloid’s GitHub and GitLab connectors, these insights become part of the review conversation, allowing teams to adjust sizing or resource types early. The difference is profound: instead of waiting for finance to flag runaway costs at the end of the month, teams prevent overspend before it happens.
Continuous Monitoring in Pipelines
FinOps doesn’t stop once a merge is approved. As deployments roll out, Cycloid integrates seamlessly with monitoring and observability tools to surface cost metrics alongside performance data. This means engineers can see not just whether a service is healthy, but also how much it costs to keep it running.
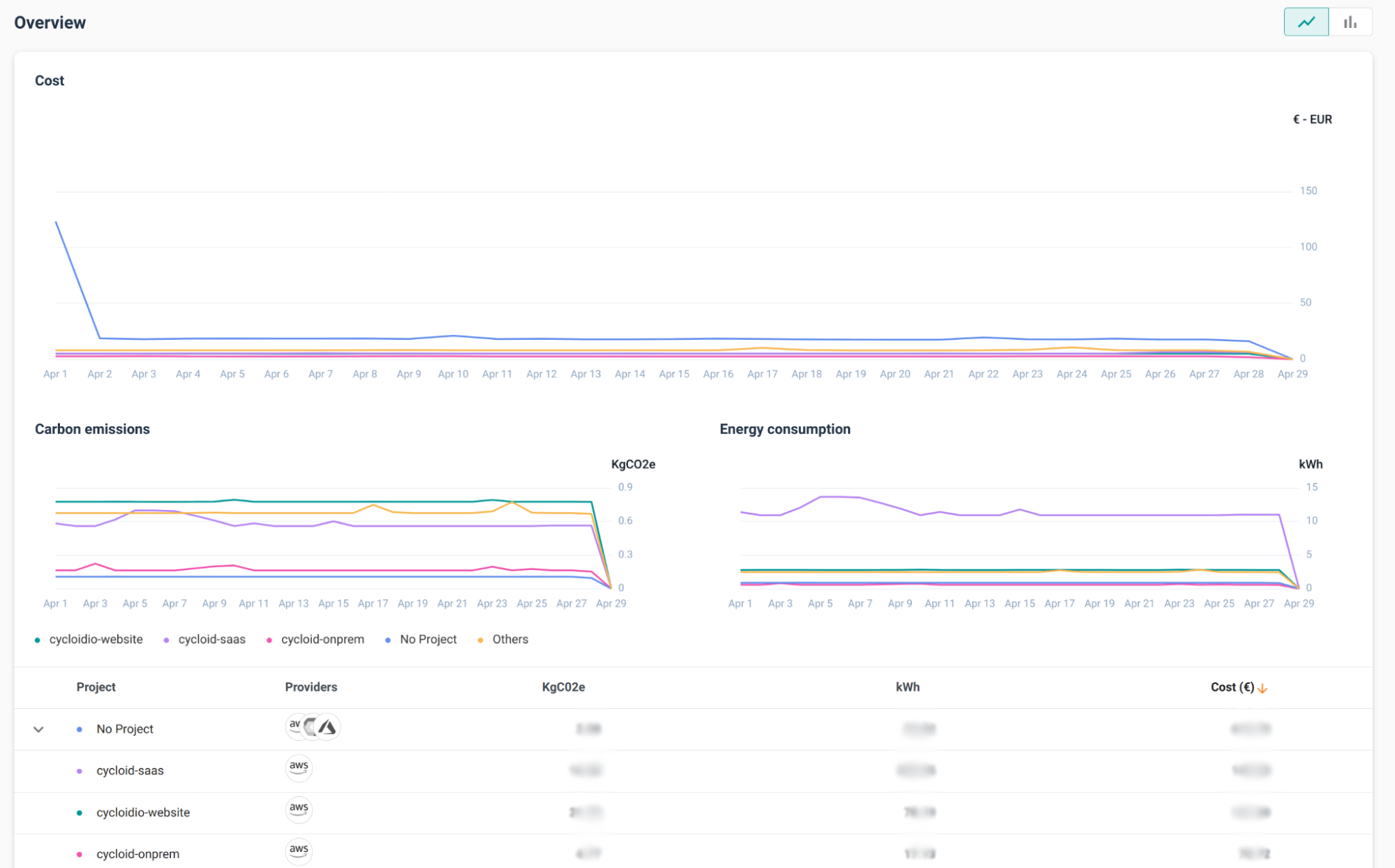
In practice, Cycloid’s pipeline templates enable organizations to create cost dashboards into their delivery process. Canary deployments, for example, can be tracked not only for error rates and latency but also for cost per request. If a new service performs well but introduces disproportionate spend, the issue can be caught during the canary stage rather than after global rollout. For teams focused on continuous delivery, this tight feedback loop ensures that cost becomes another quality signal, treated with the same urgency as failed tests or security vulnerabilities.
Branching Hygiene With FinOps (Parallel to Code Practices)
Good branching hygiene has long been part of software delivery. Developers avoid long-running branches because they create merge conflicts, stale code, and slow feedback. The same principle applies when infrastructure and cost management enter the developer workflow: short-lived, isolated changes prevent both technical and financial drift. Cycloid extends this practice to FinOps by applying cost guardrails at the branch level, ensuring that financial impact is visible and controlled in the same way as code quality.
When a feature branch introduces infrastructure changes, for example, a new Kubernetes namespace, an RDS instance, or an auto-scaling group, Cycloid treats that branch as an ephemeral environment. Through its integration with Git providers and Terraform, Cycloid spins up the resources, calculates their projected spend using its Cloud Cost Management (CCM) module, and makes those numbers available directly in the pull request.
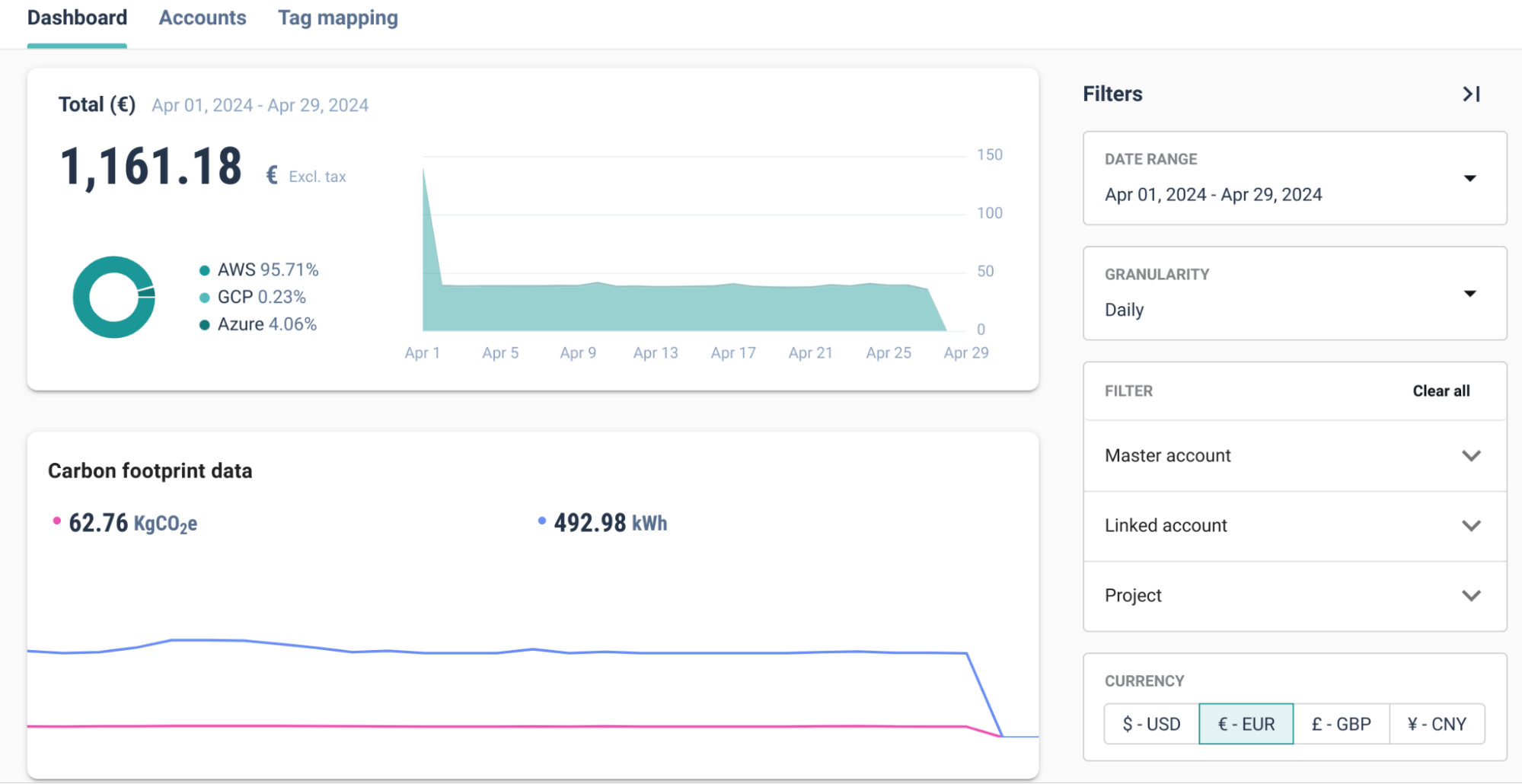
The CCM dashboard gives reviewers a breakdown of estimated spend per environment. For example, when a branch requests a larger EC2 instance type, the diff doesn’t just show the technical YAML change; it surfaces as a projected cost increase in dollars.
When the branch is merged, Cycloid automatically tears down the associated resources, preventing idle test environments from quietly consuming the budget. Pair reviews also become richer with cost insight. Instead of focusing only on the correctness of Helm charts or Terraform HCL, reviewers see cost diffs side by side with code diffs. A proposed change to increase an EC2 instance type from t3.medium to m5.2xlarge isn’t just a technical delta; it shows up as an estimated increase of several hundred dollars per month, directly flagged in the PR.
By enforcing branch-scoped cost guardrails, Cycloid ensures that experimentation remains safe, efficient, and transparent. Just as trunk-based development relies on short-lived feature branches to minimize technical debt, Cycloid’s approach minimizes cost debt, preventing runaway spend before it becomes entrenched in production.
| Category | Point Solutions | Cycloid’s Orchestration Layer Approach |
| Cost Visibility Tools | Infracost: Estimates Terraform costs pre-deploy. Kubecost: Monitors Kubernetes workloads in real time. CloudZero: Maps spent on products/teams at the business level. | Cycloid Cost Estimation API embeds cost data into pull requests, commits, and dashboards. Provides both pre-deployment estimates (via IaC) and post-deployment metrics. Developers see cost diffs alongside code diffs. |
| Deployment & Governance Tools | Terraform with policies, OPA/Gatekeeper, StackGen: Enforce rules on infra definitions, but often require multiple integrations to tie cost + governance together. | Cycloid Orchestrator applies cost and compliance policies directly in pipelines. Blocks out-of-policy or over-budget resources before deployment. Seamlessly integrates with Terraform and Git workflows for developer-first governance. |
| Observability & Monitoring | Prometheus/Grafana/Datadog: Strong performance and infra health monitoring; cost tracking requires custom tagging and manual dashboards. | Cycloid dashboards unify cost with performance. Shows cost-per-request, cost-per-environment, and ties to existing observability stacks. Developers and SREs treat cost as a first-class health metric. |
Migration Path: From Finance-Owned to Team-Owned FinOps
Shifting FinOps responsibility from finance-only to a shared engineering practice is not an overnight process. It requires incremental adoption, cultural change, and the right tooling embedded into developer workflows. Cycloid supports this transition by giving teams both visibility and guardrails at each stage, so FinOps matures in parallel with delivery practices.
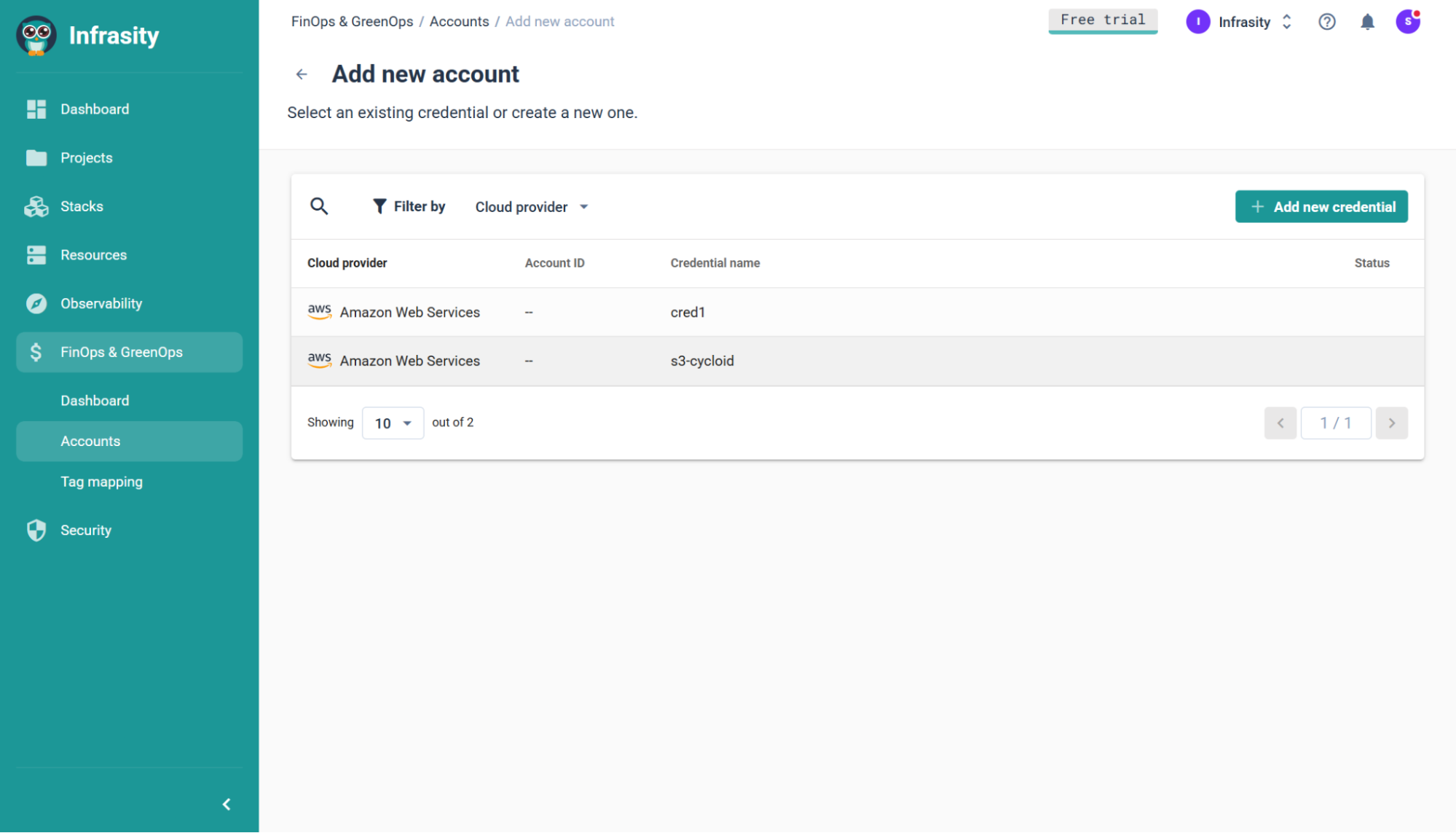
Step 1: Baseline spend and connect cloud accounts.
Create an authoritative baseline by enabling cloud billing exports (AWS Cost & Usage, GCP Billing export, Azure Cost Management) and connecting those accounts into Cycloid so that billing data is ingested into Cycloid reporting. Confirm tags and resource metadata are included in the export so Cycloid can map spend to projects/environments.
Step 2: Enforce tagging and canonical naming in IaC.
Add tag-enforcement checks to your Terraform modules (required tags: team, service, environment, cost-center) and add a Cycloid policy that rejects or flags infra changes missing those tags at plan-time. Ensure your module templates include example tag variables and a policy test in CI.
Step 3: Add a pre-merge cost-estimation stage (Terraform plan → Infracost).
In every repo pipeline, add an early stage that runs terraform plan -out=tfplan, then terraform show -json tfplan > plan.json and pipes that into Infracost to produce a PR cost diff. Use Cycloid’s Git connector to post the Infracost summary into the PR as a comment and attach the JSON artifact to the build. Keep the cost stage fast and fail-safe (non-blocking initially).
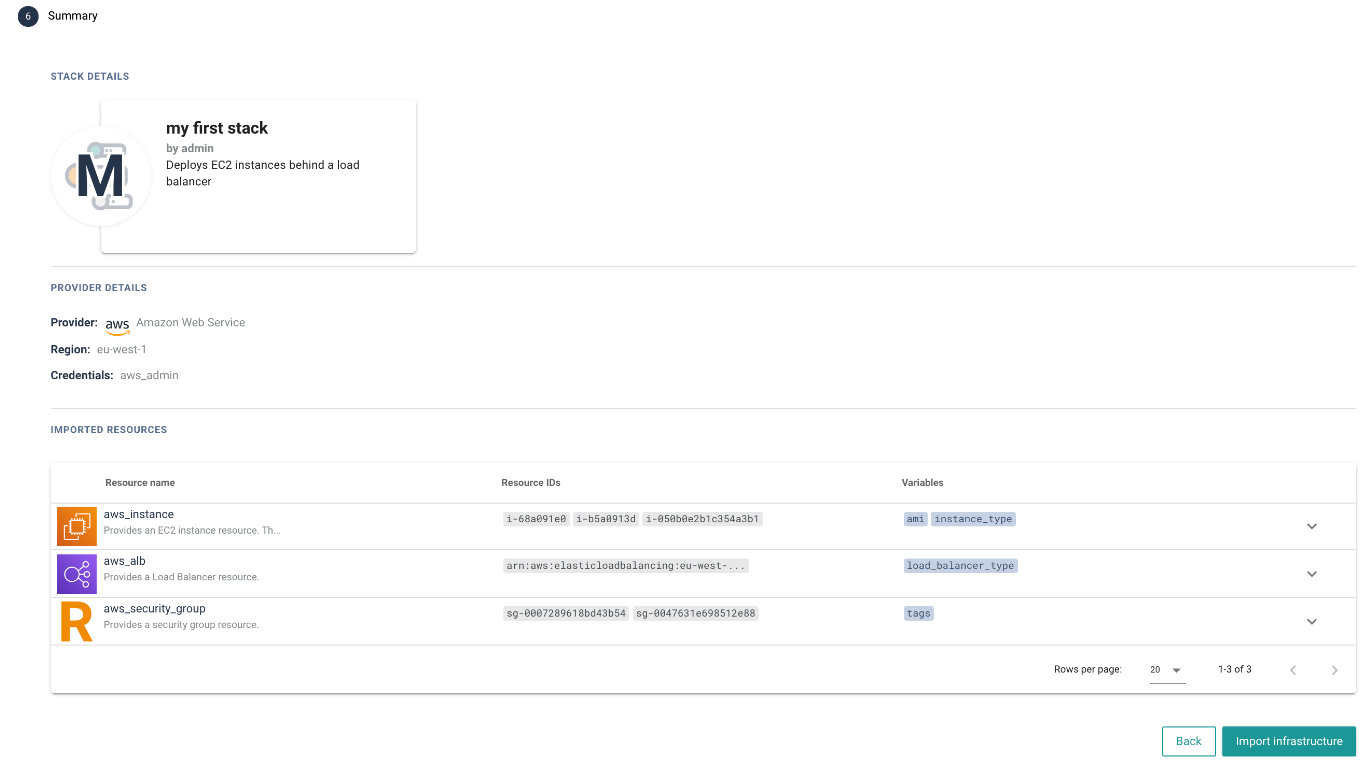
In this step you can view the summary of all the data that has been added throughout the wizard:
- The Stack card preview
- The Provider details (Also, Project and External Backend info in the Create Stack & Project mode)
- A table of selected resource types with the resource IDs and variables. You can expand each list item to see all the related resources/variables
You can go back to the previous steps to make any adjustments. When the configuration looks good click the Import infrastructure button to begin the import!
Step 4: Introduce a cost-gate policy on PRs.
Create a Cycloid policy that evaluates the Infracost/plan output and compares it against pre-set thresholds (absolute $ limit and % delta). Wire the policy evaluator into the pipeline as a policy-check step that can return warn or fail. Start with warn mode, then flip to fail after team buy-in.
Step 5: Make environments ephemeral and branch-scoped.
Configure Cycloid environment templates that map feature branches to ephemeral environments. Ensure the pipeline provisions ephemeral infra for the branch, sets a TTL (e.g., 2 hours / 24 hours), and automatically tears down the environment on branch close. Include a cost cap metadata field on the environment object so cost dashboards can attribute and limit spend per branch.
Step 6: Wire cost telemetry into canary runs.
Extend your pipeline templates so canary stages emit cost-related metrics (cost-per-request, cost-per-second) into your observability stack. During a canary deployment, compare performance delta and cost-per-request; if cost rises disproportionately, automatically rollback or pause rollout. Use Cycloid pipeline templating to ensure all services run the same canary + cost-check sequence.
Step 7: Apply progressive enforcement and guardrails.
Phase enforcement: start with visibility (PR comments, dashboards), then move to soft enforcement (policy warn), and finally hard enforcement (pipeline fail/block and required approvers). For high-risk namespaces or production accounts, enable stricter enforcement and require human approval for overrides. Record all actions in the audit logs for compliance.
Boom! You have successfully shifted FinOps responsibility from finance-only to a shared engineering practice.
Decision Guide: When Cost Ownership Shifts to Developers
There is no single point in time when every organization must hand FinOps responsibilities to developers. The right timing depends heavily on team structure, delivery model, and industry requirements. What Cycloid provides is the ability to progressively distribute cost ownership with the right guardrails in place. The following scenarios illustrate how and when that shift typically happens.
| Scenario | Recommendation with Cycloid |
| Fast-scaling startup, daily deploys | Use Cycloid pipeline checks + Infracost so every pull request shows cost diffs before merge. Developers own cost awareness as part of daily CI/CD. |
| Enterprise with centralized FinOps | Adopt a hybrid model: finance sets global thresholds, while developers enforce them locally with Cycloid policy engine in pipelines. |
| Teams using serverless heavily | Expose Cycloid APIs + real-time cost telemetry to track cost-per-request/invocation. Developers tune workloads with live financial feedback. |
| Compliance-heavy organizations (banking, healthcare, etc.) | Enable Cycloid guardrails with audit-ready logs, so developers make cost decisions under strict governance and every change is recorded for compliance. |
Conclusion
FinOps is no longer a finance-only exercise; it has become a developer responsibility. As cloud adoption accelerates and delivery cycles shorten, the ability to prevent cost overruns depends on embedding financial awareness directly into engineering workflows. Just as security and testing shifted left, cost control must follow the same path.
Cycloid enables this shift by moving FinOps into the orchestration layer, the place where infrastructure definitions, CI/CD pipelines, and developer actions converge. Instead of surfacing costs after the fact, Cycloid makes them visible before deployment, integrates policy checks into pull requests, and provides dashboards that unify performance with financial metrics. The result is a workflow where cost awareness is invisible until it needs to be actionable, empowering developers to make financially sound decisions without slowing down delivery.
For organizations, the benefit is twofold: predictable cloud bills and teams that align technical choices with business goals. For developers, FinOps becomes another dimension of quality, alongside performance, reliability, and security. With Cycloid, everyone owns cost awareness, and no one is left waiting for the end-of-month invoice to learn what went wrong.
FAQs
1. Can developers really influence cloud bills meaningfully with Cycloid?
Yes. By surfacing cost diffs in pull requests and integrating Infracost with Cycloid pipelines, developers see the impact of their changes before merge. This allows them to adjust instance sizes, storage tiers, or scaling policies proactively, reducing costs before infrastructure is even provisioned.
2. How do Cycloid APIs help embed FinOps into daily workflows?
Cycloid exposes APIs for cost estimation, policy evaluation, and reporting. These APIs can be plugged into CI/CD pipelines, GitHub or GitLab connectors, and even IDE extensions. This means developers receive cost feedback alongside test results and linting, making FinOps part of their daily loop.
3. Is FinOps relevant for small teams, or only enterprises?
Both. For small teams, FinOps ensures that scaling doesn’t lead to unexpected bills, especially when using ephemeral environments or serverless platforms. For enterprises, Cycloid enforces consistent cost policies across multiple teams and clouds, ensuring compliance and predictability at scale.
4. How does Cycloid balance developer velocity with cost governance?
Instead of introducing manual approval steps, Cycloid automates cost checks and guardrails inside pipelines. Developers continue to move quickly, but resources that break defined cost thresholds are flagged or blocked automatically. This creates a balance where velocity is preserved, but financial discipline is maintained.