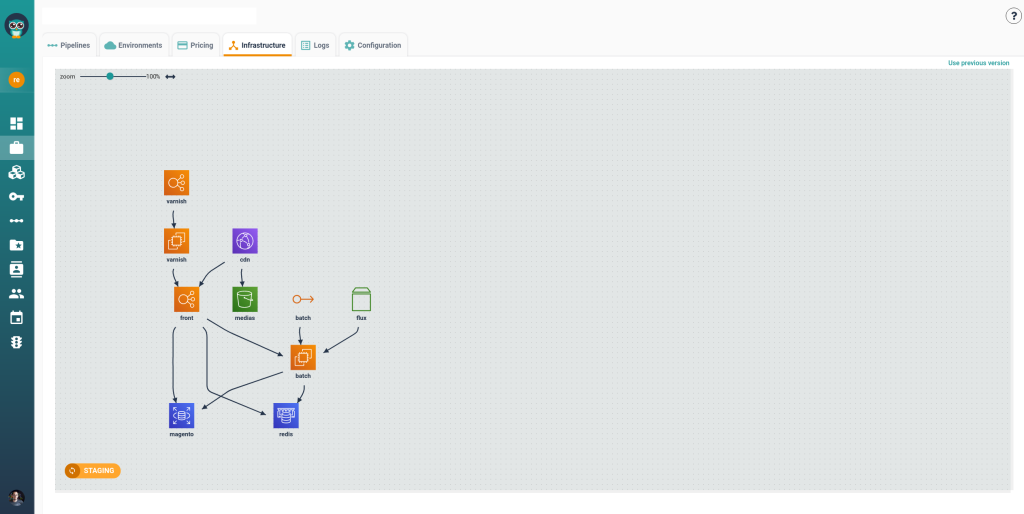
TL;DR
- MSPs often struggle with scattered cloud access, inconsistent provisioning, and lack of client isolation.
- A Cloud Management Portal (CMP) tailored for MSPs helps centralize infra control, enable team-specific access, and automate resource provisioning.
- Cycloid offers a multi-tenant CMP built for MSP workflows, where each client is isolated into a “Project” with dedicated environments.
- With reusable infrastructure stacks, role-based access control, and cost estimation built-in, Cycloid lets MSPs deliver cloud services at speed, without compromising security or consistency.
Imagine being a Solution Architect at a Managed Service Provider (MSP), juggling infrastructure for a dozen clients, each with unique stacks, environments, access requirements, and compliance rules. One day you’re provisioning Kubernetes clusters for a fintech startup, and the next, you’re managing backups for a healthcare provider. Now multiply that complexity by 20 clients.
Sounds chaotic? It usually is, until you adopt a cloud management portal designed for multi-tenancy.
This guide walks through how MSPs can simplify cloud operations using a platform like Cycloid, built from the ground up for client isolation, RBAC enforcement, and infrastructure as a service, without having to code everything from scratch.
What is a Cloud Management Portal (CMP) for MSPs?
In the MSP world, CMP management isn’t about a single account or one client. It’s about securely managing many, without losing control or visibility.
A Cloud Management Portal for MSPs is a centralized platform that allows teams to manage cloud infrastructure for multiple clients from a single control plane. It abstracts the operational complexity of provisioning, securing, and scaling cloud resources across different accounts, environments, and service providers.
CMP vs Generic Cloud Dashboards
Generic cloud dashboards, like the AWS Console or Azure Portal, were built with individual organizations in mind, not multi-client MSP use cases. While these portals are powerful, they assume:
- A single identity provider
- Shared resource visibility
- Homogeneous teams with overlapping access
That falls apart fast in an MSP context, where:
- Each client must be logically and operationally isolated
- Resource visibility needs to be scoped per project
- Teams require strict boundaries, permissions, and audit history
- Branding, cost controls, and compliance vary per tenant
What Makes an MSP-Oriented CMP Different?
Let’s break down the essential traits of a CMP cloud built for MSPs like Cycloid:
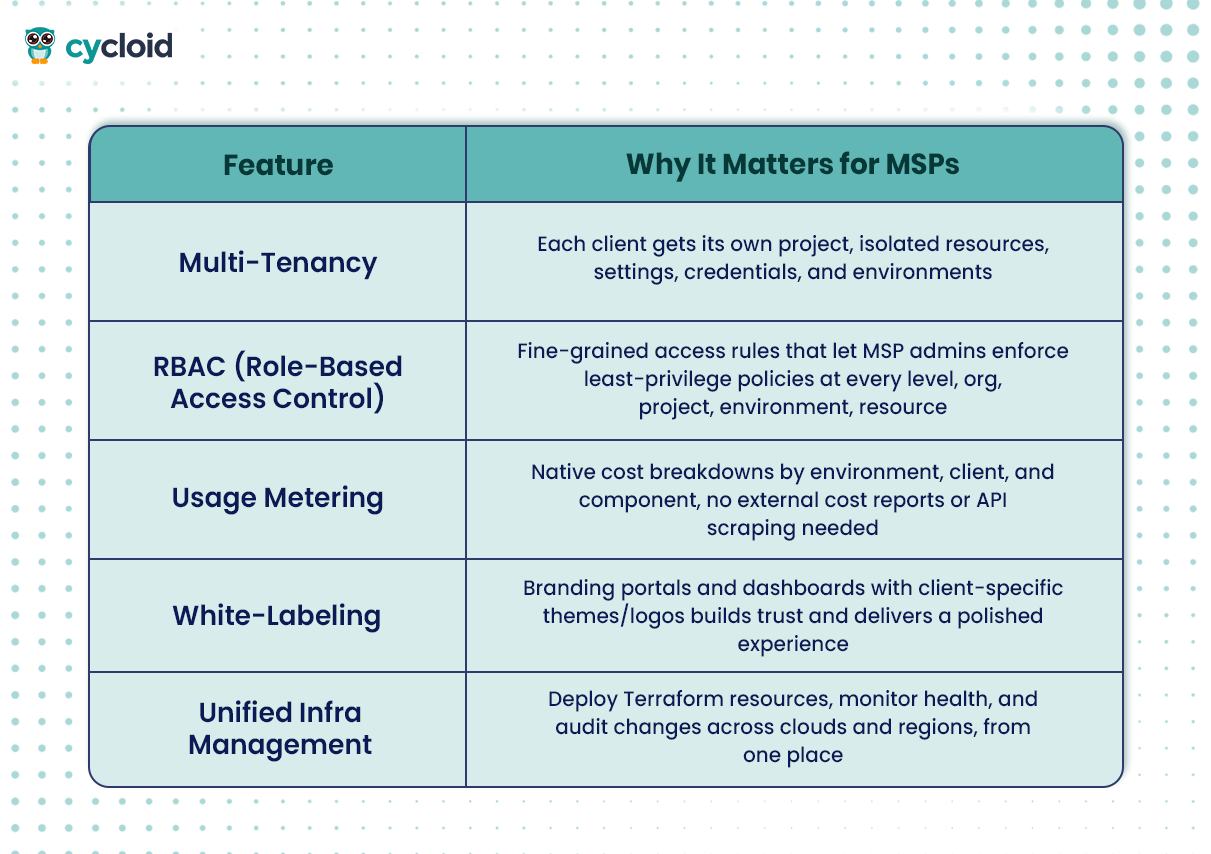
Why Native Consoles Break Down for MSPs
When an MSP scales beyond 2–3 clients, vendor-native tools start to show cracks:
- Account/Subscription Sprawl: Every new client means another AWS account or Azure subscription to track manually.
- Access Overhead: IAM roles and permissions need to be handcrafted and audited for every team and environment.
- Provisioning Consistency: Reusing Terraform modules across projects requires scripting, pipelines, and custom UIs.
Managing Infrastructure Chaos as an MSP Architect
As a Solution Architect at an MSP, you’re constantly balancing the needs of multiple clients, and each one comes with their own flavor of complexity. One client demands fine-grained access control across teams, another wants multi-cloud resource provisioning with billing alerts, and a third expects secure, auditable infrastructure for their regulated workloads.
At a small scale, it’s manageable. You script some Terraform, manually configure IAM, and track billing via CSV exports. But once you hit a dozen clients, things start to break.
The Real-World Mess MSPs Deal With
- Duplicated Infrastructure Code: You’re maintaining the same Terraform or Pulumi logic for 10 different clients, each slightly tweaked and living in different Git repos.
- Siloed Access Models: No unified RBAC strategy. IAM roles, service accounts, and SSH keys vary wildly between clients, risking privilege creep or accidental exposure.
- Fragmented Visibility: Want to see which projects are costing the most this quarter? That means logging into each provider’s console individually, pulling reports, and building spreadsheets.
In short, you’re managing chaos, and that chaos scales with every new client you onboard.
Control Plane for MSPs
Cycloid flips this model on its head.
Rather than treating every client as a new infrastructure headache, Cycloid gives you a structured, multi-tenant control plane where each client lives in its own project, isolated by design, but unified in view.
You don’t start from scratch. You start with boundaries, defaults, and reusable infrastructure logic that fits every new client into your system, not the other way around.
Cycloid’s Multi-Tenant Project Structure
At the heart of Cycloid’s approach to multi-tenancy is the Project. Each project in Cycloid represents a completely isolated client workspace, with its own environments, infrastructure, identity model, and metadata.
This isn’t just a logical naming system, its full operational and security isolation, baked in.
Projects as Isolated Client Workspaces
Let’s say you’re already managing two clients, Acme Corp and Finlytics. Each one is represented in Cycloid as a separate project. Now, you’ve onboarded a third client, NetSecure, and need to provision their infrastructure.
You don’t duplicate code or set up another CI pipeline.
You simply create a new project in Cycloid.
Behind the scenes:
- Identity providers are scoped to that project (SSO, SCIM, SAML, or Keycloak realms)
- Environments are isolated (e.g., dev, staging, prod)
- Infra deployments, cost reporting, and activity logs are tracked per project
- Resource tags and Terraform variables inherit from the project context.
Cycloid Visual Hierarchy
| Cycloid Portal ├── Project: Acme Corp │ └── Environments: dev, staging, prod ├── Project: Finlytics │ └── Environments: prod ├── Project: NetSecure │ └── Environments: staging, prod |
In just a few clicks, you can go from managing two clients to managing ten, each with the same structural guarantees and operational consistency.This project-first design is what makes Cycloid viable not just as a dashboard, but as a true multi-tenant CMP for Managed Service Providers.
Real-World Scenario, Adding a New Client
Let’s pick up the story. Our Solution Architect is already managing two clients in Cycloid, each with isolated environments, infrastructure deployments, and access rules scoped to its own project.Now, a third client is coming on board.In a traditional setup, onboarding would involve:
- Duplicating Terraform templates
- Creating IAM roles and RBAC bindings manually
- Configuring separate dashboards
- Writing custom automation to ensure everything stays separated
With Cycloid, this process is vastly simplified.
Step 1: Creating a New Project
Inside Cycloid, the architect clicks “Create Project” and enters a few key details:
- Project Name: NetSecure
- Client Tag: netsecure-prod
- Cloud Provider: AWS
- Default Environments: staging, prod
This isn’t just for display, it initializes an entirely scoped workspace.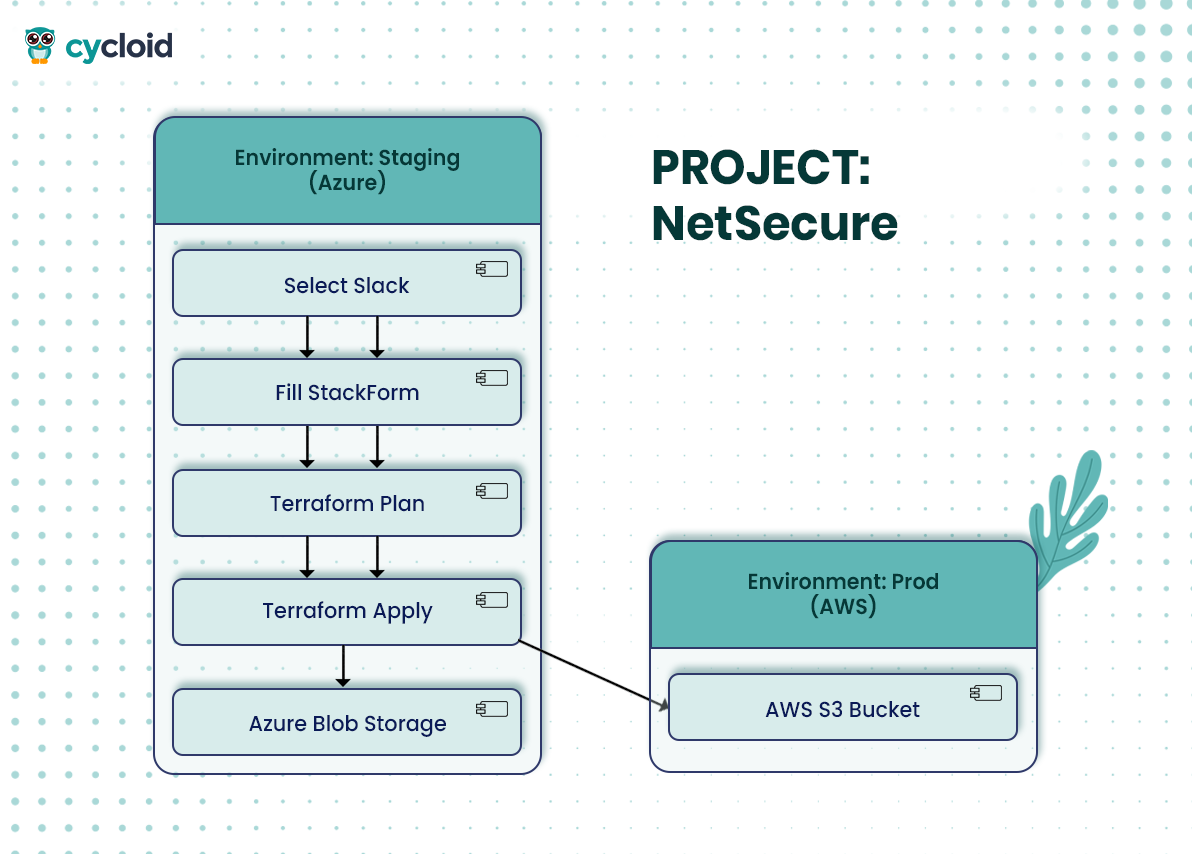 Cycloid instantly
Cycloid instantly
- Applies default RBAC roles based on the MSP’s project policy template (e.g., Admin, Developer, Cost Viewer)
- Auto-generates a workspace directory structure with placeholders for environments
- Injects standardized resource tags and metadata like project, env, and owner
Links to pre-approved infrastructure stacks that the MSP already uses internally
Step 2: Reusing Infrastructure Logic Without Duplication
The beauty of Cycloid’s architecture lies in inheritance and presets.The same Terraform modules or Helm charts used for Client-A and Client-B can now be reused, without copying or refactoring, because they’re wrapped in Stacks. These stacks are versioned, parameterized, and surfaced to users via form-driven interfaces (StackForms).You’re not duplicating YAML or modules, you’re scaling infra through reusable, declarative abstractions.
Step 3: All Clients, One Unified View
Once the third project is set up, it appears alongside the others in Cycloid’s unified interface:
| Cycloid Dashboard ├── Acme Corp │ └── Resources: 27 ├── Finlytics │ └── Resources: 18 ├── NetSecure │ └── Resources: 0 (newly initialized) |
The architect can:
- Filter by project, cloud provider, or deployment status
- Monitor activity logs and cost summaries across clients
- Manage access and approval workflows without switching portals or identities
This is the kind of operational simplicity that MSPs rarely experience in the native cloud console world.
Environments Within Projects, Logical Grouping for Real Use CasesOnce the NetSecure project is created, the architect begins the second phase: environment setup.In Cycloid, environments are more than just folders, they are isolated infrastructure scopes nested inside a project. Think of them as the logical subdivisions of a client’s cloud real estate.
Why Environments MatterLet’s say NetSecure wants:
- A staging environment in Azure to test data ingestion workflows
- A production environment in AWS to serve end users with strict compliance boundaries
Each of these must:
- Live in its own cloud account or subscription.
- Have separate RBAC rules (devs can’t touch prod).
- Be tagged distinctly for billing and reporting.
- Be independently auditable.
Cycloid enables this by enforcing separation at the environment level.Every environment:
- Has its own infrastructure state.
- Tracks its own Terraform plans and applies.
- Can restrict access based on environment-level roles.
- Has its own resource inventory and cost summary.
This is crucial for MSPs that need to bill environments separately or apply different SLAs based on workload type.
Tailored Infrastructure per Environment
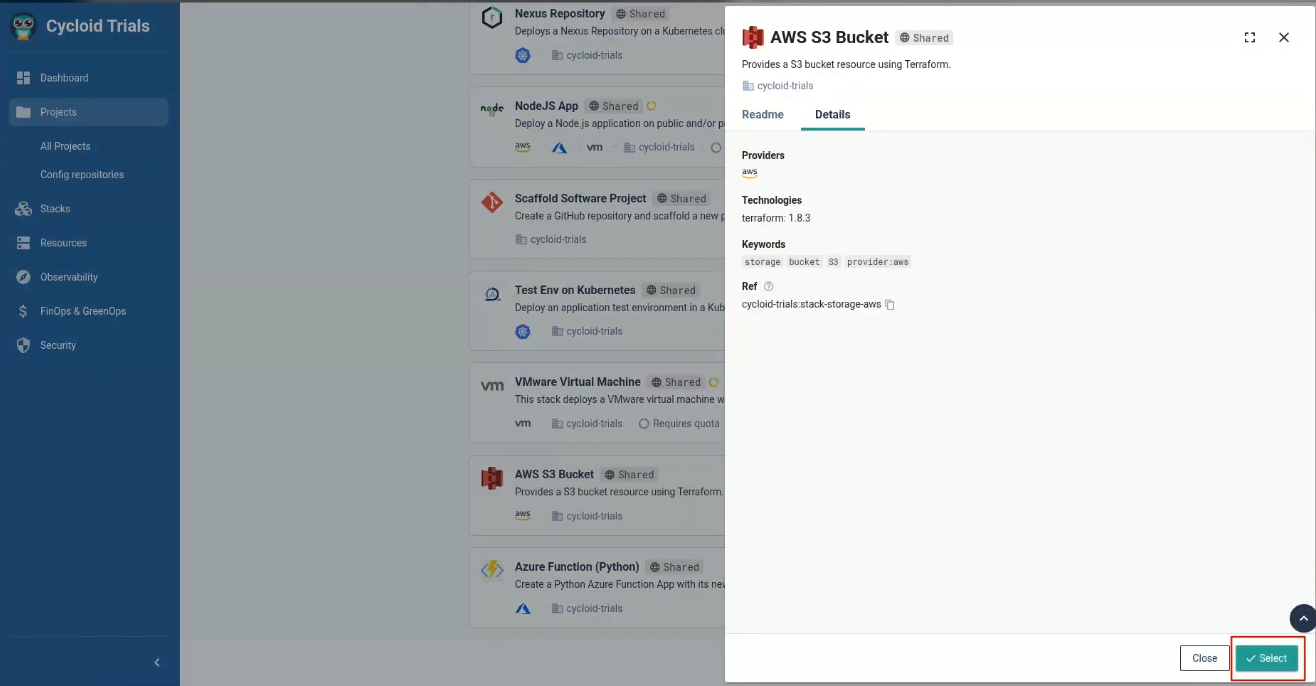
Cycloid environments are not constrained to a single provider or region.In practice:
- Staging might run in Azure East US (to align with the dev team’s location)
- Prod might run in AWS Frankfurt (to meet GDPR compliance for European users)
Cycloid’s environment definitions let the architect: Attach different cloud credentials and secrets per environment, Define separate stacks (e.g., S3 + EC2 in prod, Azure Blob in staging), and Monitor deployments and logs in isolation.
Example configuration view inside Cycloid:
| project: netsecure environments: – name: staging provider: azure region: eastus RBAC: dev-team, viewer – name: prod provider: aws region: eu-central-1 RBAC: ops-team, approver |
Each environment acts like a “mini cloud tenant” within the project, giving MSPs total control over compliance, access, and billing, without needing to manage it all manually.
Deploying Infrastructure Using Cycloid’s Stacks & StackForms
With the new NetSecure project and its environments ready, the architect moves on to provisioning infrastructure.Traditionally, this would involve writing Terraform modules, validating inputs, wiring secrets, and hand-coding apply scripts, a time-consuming and error-prone process. But with Cycloid, infrastructure provisioning is abstracted into modular, reusable building blocks called Stacks.
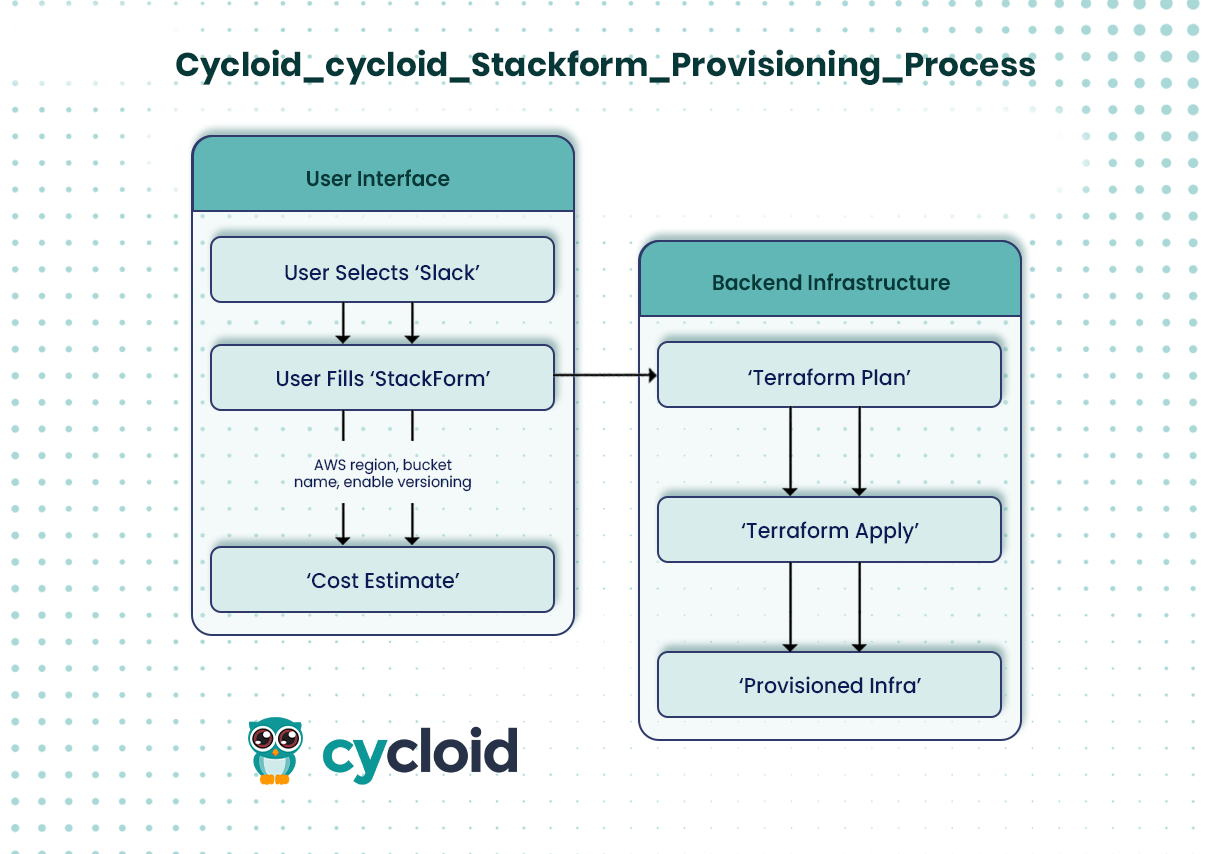
Reusable, Versioned Stacks
A Stack in Cycloid is a packaged, versioned infrastructure template built on Terraform (or other IaC tooling). It encapsulates:
- Infrastructure code (e.g., AWS S3, GKE, Azure Functions)
- Input schemas and validations
- Policies and organizational defaults
- Output expectations and lifecycle rules
Stacks are created once by experienced engineers and can be reused across clients and environments without modification.
This means:
- Non-Terraform users can deploy cloud infrastructure safely, without touching code
- Terraform users retain full control, versioning, and customizability
- MSPs gain consistency and guardrails across all projects
In the NetSecure example, the architect wants to provision an S3 bucket inside the prod environment. Instead of writing HCL, they select the aws-s3-stack from Cycloid’s Stack catalog.
StackForms: Terraform Without Writing Code
When deploying from a Stack, Cycloid presents a StackForm, a clean, form-driven UI to input infrastructure parameters. The form is auto-generated from the Stack’s Terraform input schema and includes validations, dropdowns, and tooltips.Here’s what the S3 StackForm might look like: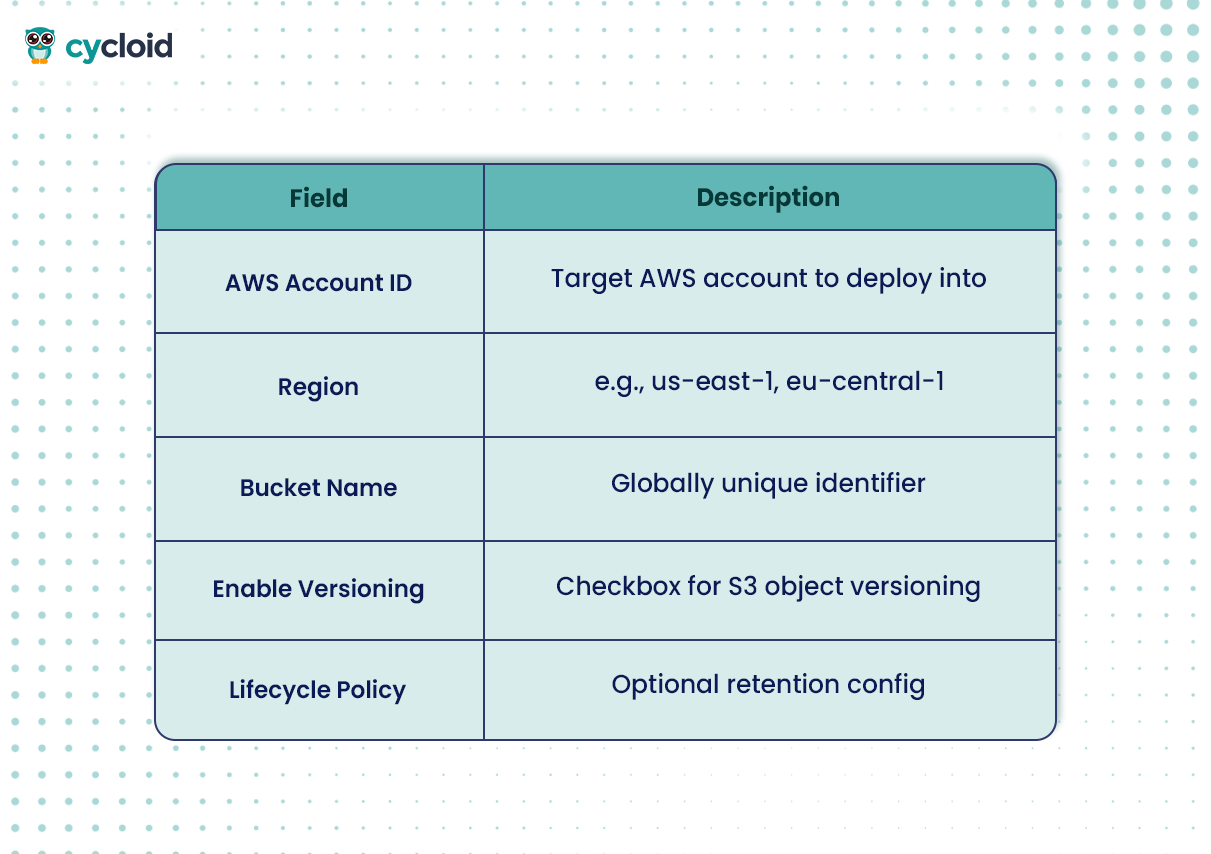
This form allows developers, ops, or even project managers to provision infrastructure without touching a terminal, while still using Terraform under the hood.
No YAML. No TF files. No guesswork.
Role-Based Access Control (RBAC) Done Right
As infrastructure scales across clients, so does the need for tight access control. Cycloid’s RBAC model is designed specifically for multi-tenant, multi-team environments like MSPs.
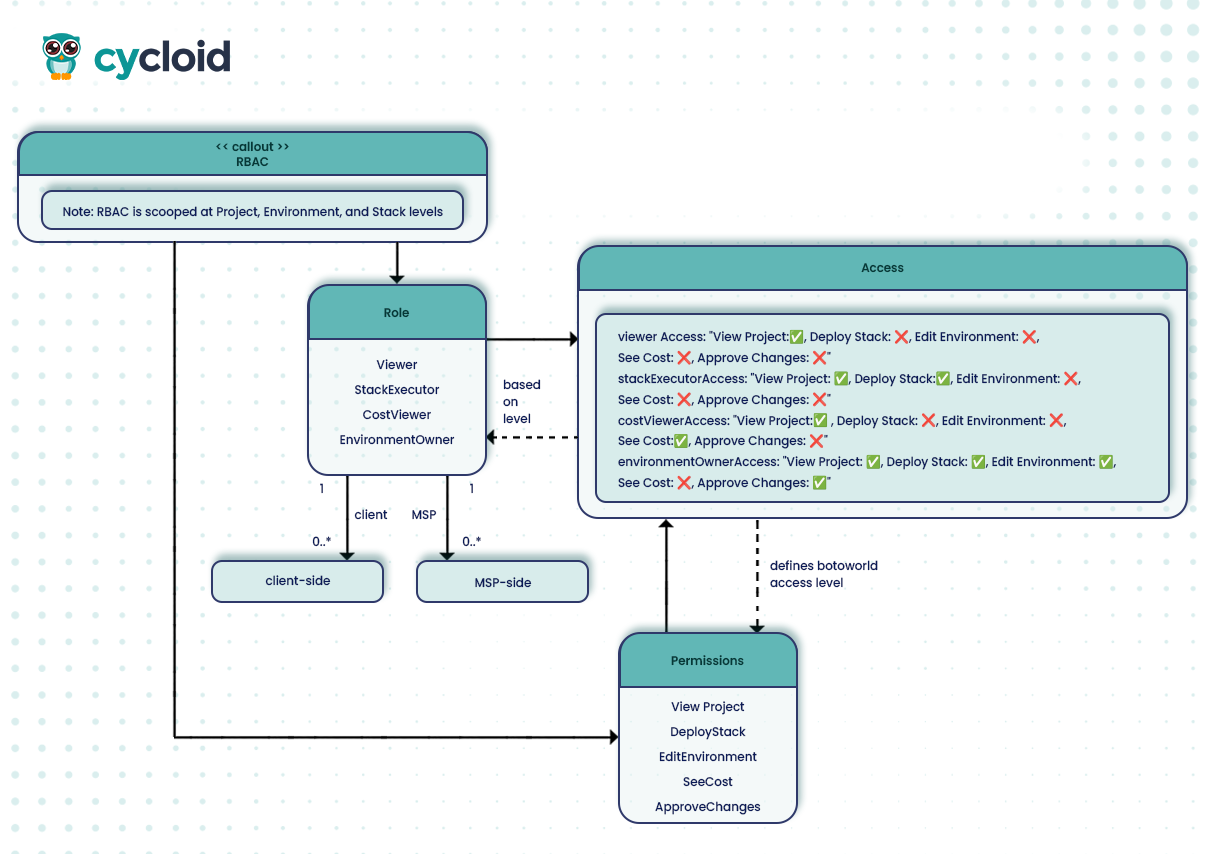
Multi-Layered Access Controls
RBAC in Cycloid is hierarchical and scoped to multiple levels: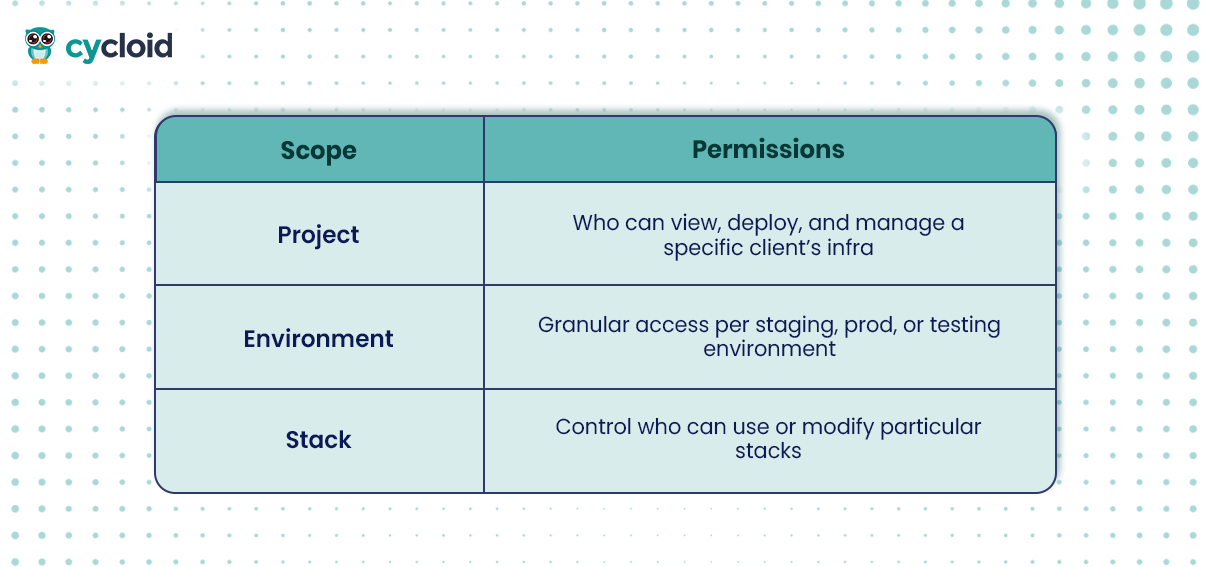
Cycloid includes pre-defined role templates aligned to common MSP workflows:
- Project Viewer – Read-only access to a client’s dashboard and resource metadata
- Stack Executor – Can deploy stacks but cannot edit templates or policies
- Cost Viewer – Sees usage and cost reports, ideal for finance or account managers
- Environment Owner – Full control over a specific environment (e.g., prod)
Each role can be customized to match your organization’s structure or tenant-specific policies, and integrates with SSO or SCIM for easy onboarding.
 RBAC Analogy for Client TeamsThink of Cycloid’s RBAC model like managing keys to three different buildings, where:
RBAC Analogy for Client TeamsThink of Cycloid’s RBAC model like managing keys to three different buildings, where:
- Each building is a client project
- Each floor is an environment
- Each room is a stack or resource
Now:
- NetSecure’s developers can access staging, but not prod
- Their billing team can only see the cost reports
- Only MSP operators can edit stacks and apply changes
This model ensures zero trust by default, while still enabling flexible access for internal and external teams.
End-to-End View: Why Cycloid Fits MSP Workflows
Cycloid isn’t just another dashboard layered on top of cloud accounts, it’s a purpose-built control plane designed to meet the messy, multi-client reality that Managed Service Providers live in daily.Here’s how it addresses the core operational pain points MSPs face.
1. Centralized Yet Isolated
Cycloid gives MSPs one central place to manage all clients, without overlap or compromise.
- Each client is represented as an isolated Project, with its own environments, resources, users, and deployment history.
- You can switch between projects instantly, but under the hood, every action is logged, scoped, and auditable to prevent accidental access or cross-tenant contamination.
- Audit-ready: All deployments, user actions, and cost reports are traceable per project and per environment, critical for SOC 2, ISO 27001, or client-specific governance.
2. Deployment Speed Without Compromise
Fast doesn’t have to mean risky.With StackForms, Cycloid delivers a no-code provisioning layer that non-expert users can operate, while still using version-controlled Terraform behind the scenes.
- Pre-approved, reusable stacks = consistency across deployments
- Inputs and parameters are validated and scoped, reducing runtime errors
- Supports hybrid and multi-cloud infrastructure (e.g., AWS S3, Azure Functions, GCP Compute) without switching cloud management tools
3. Built-In DevOps for MSP Teams
Cycloid comes with DevOps features that MSP teams would otherwise spend months building and maintaining:
- CI/CD pipelines to run Terraform plan/apply in controlled stages
- Cost estimation and breakdowns built into the deployment UI
- Logs tied to every project and environment
- Monitoring hooks for external MSP tools (e.g., Prometheus, Datadog)
- Audit logs for every action, accessible by project or role
This eliminates the need to glue together 5–6 third-party cloud cost management tools just to deliver compliant infrastructure at scale.The result? You spend less time building internal tooling, and more time delivering value to clients.
Conclusion
Managing infrastructure for multiple clients is rarely straightforward, especially when each has their own environments, access models, and compliance boundaries. For MSPs, stitching together cloud-native consoles, homegrown scripts, and permission models quickly turns into a fragile, manual process. Cycloid redefines that experience by offering a multi-tenant control plane purpose-built for MSP workflows, where each client is a fully isolated project with reusable infrastructure, fine-grained RBAC, and integrated cost forecasting.In this guide, we walked through how Cycloid enables MSPs to onboard new clients without code duplication, structure environments for compliance, deploy infrastructure using form-driven Stacks, and control access with zero-trust RBAC. More than a dashboard, it’s a structured system for scaling infrastructure delivery securely and efficiently, client by client.
FAQs
1. What is MSP in cloud computing?
An MSP (Managed Service Provider) is a third-party company that remotely manages a client’s IT infrastructure and cloud services. MSPs typically handle provisioning, monitoring, cost optimization, security, and support across cloud environments on behalf of multiple customers.
2. What is a cloud management portal?
A cloud management portal (CMP) is a centralized interface that allows organizations to control, monitor, and provision cloud infrastructure across different providers. For MSPs, CMPs must support multi-tenancy, access controls, reusable templates, and cost visibility across many clients.
3. What is the best cloud management platform?
The best CMP depends on your use case. For MSPs managing multiple clients and environments, Cycloid stands out by combining infrastructure-as-code, RBAC, cost estimation, and environment isolation, all inside one unified portal purpose-built for service providers.
4. What is an MSP portal?
An MSP portal is a secure platform used by Managed Service Providers to deliver, manage, and monitor services across multiple clients. It typically includes multi-tenant support, user access management, resource provisioning, and audit features, enabling MSPs to scale without losing control.