Cloud Management Platforms (CMPs) abstract the underlying complexity of provisioning, managing, and securing infrastructure across cloud providers. A CMP can expose a unified Terraform catalog that provisions infrastructure in any combination of public and private clouds, such as AWS, Azure and VMware. For DevOps and platform engineering teams juggling multiple accounts, tools, and policies, CMPs offer a centralized control layer focused on governance and compliance, not day-to-day developer workflows.
In this article, we’ll unpack the core differences between Cloud Management Platforms and Internal Developer Platforms (IDPs), explain when and why to use each, and show how they can work together in the same organization without conflict. We’ll also walk through a hands-on example of abstracting AWS infrastructure using Terraform and explore why unified platforms like Cycloid are used for combining both approaches without adding operational overhead. By the end, you’ll have a clear understanding of which abstraction layer, or combination, is the right fit for your platform engineering team.
What CMPs Actually Do in a Multi-Cloud Environment
At their core, Cloud Management Platforms unify and standardize infrastructure management across providers like AWS, Azure, VMware and Google Cloud. Instead of forcing every team to reinvent provisioning, policy enforcement, and cost tracking, Cloud Management Platforms let organizations:
- Centralize account provisioning: Instead of manually setting up projects in GCP or accounts in AWS, a CMP like Morpheus can auto-create them with preconfigured VPCs, IAM roles, and tagging policies, so new teams get secure, ready-to-use environments in minutes.
- Apply consistent IAM policies: With a CMP, platform teams can define access rules once, like “DevOps engineers get read/write access to staging”, and apply them across AWS IAM, Azure AD, and GCP IAM, avoiding gaps or manual errors.
- Enforce quotas and budgets: Tools like Cycloid can cap spending or limit resources. If someone tries to exceed it, the platform gets alerted—or blocked automatically.
Think of CMPs as the “governance layer” for cloud infrastructure. They don’t define how developers ship apps, but they define where and under what constraints apps can run.
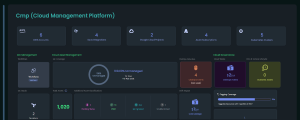
Core Parameters in CMPs
- Cloud Inventory: Tracks Kubernetes clusters and cloud accounts (AWS, GCP, Azure) to give visibility into managed/unmanaged resources.
- IaC Workflows & Explorer: Supports reusable infrastructure workflows and visualizes IaC structure, drift, and ownership.
- Integrations: Connects with GitHub, Terraform Cloud, etc., to map resources back to source and detect out-of-band changes (ClickOps).
- Governance Metrics: Shows IaC coverage, flags unused resources (Cloud Waste), and promotes compliance through drift detection.
- GitOps & ChatOps: Ties infrastructure actions into version control and collaboration tools for safer, automated changes.
For example, a CMP can give your compliance officer a single dashboard to view all GCP billing reports, AWS IAM policies, and Azure security group changes, without having to log into each console.
CMPs Are Generally Run by CloudOps, Not AppDev
While CMPs support self-service infrastructure provisioning, they’re typically geared toward platform engineers and administrators — not optimized for day-to-day developer workflows like deploying, testing, or debugging services. They’re built for infrastructure and cloud operations teams whose priorities are:
- Cost control: 49% of businesses struggle to keep cloud costs under control, and 33% exceed their budgets by 40% or more.
- Multi-cloud orchestration: 28% of public cloud spending is wasted annually due to overprovisioning and underutilization.
When to Use an Internal Developer Platform: Enable Self-Service for Application Teams
Internal Developer Platforms (IDPs) are purpose-built to streamline the developer experience by providing self-service workflows, simplifying deployment pipelines, and abstracting infrastructure complexity. While Cloud Management Platforms (CMPs) focus on governance, cost control, and centralized infrastructure provisioning, IDPs focus on developer self-service and application delivery.
If a Cloud Management Platforms is about setting up the roads, traffic rules, and toll gates, an IDP is the navigation app that helps drivers reach their destination without worrying about what’s underneath. Developers don’t need to understand VPCs, IAM policies, or Terraform modules—they just select a template, push code to Git, and deploy
What IDPs Actually Do for Developers
An Internal developer portal allows engineers to ship software without needing to understand Kubernetes, Terraform, or cloud IAM policies. Platform teams use IDPs to expose common operational tasks, like spinning up an environment or deploying a service, as reusable, self-service actions.
For example:
- Instead of writing Helm charts or Terraform modules, a developer selects a “Deploy to Staging” button backed by a pre-configured Kubernetes template.
- To create a new environment for feature testing, a developer fills out a simple form, while the platform handles naming, ingress rules, secret injection, and autoscaling.
This interface can take many forms: a UI (like Backstage), a CLI (like pctl), or even GitOps-style pull requests driven by templates.
Use Cases Where IDPs Shine
IDPs platform are most valuable in product-focused engineering orgs where platform teams want to reduce friction for developers while maintaining control over infrastructure standards. Key use cases include:
- Creating ephemeral environments for pull requests, QA testing, or demos
- Deploying microservices to Kubernetes with baked-in policies (e.g., resource limits, network rules)
- Triggering CI/CD workflows through GitOps, pipelines, or self-service actions
- Provisioning managed services like Postgres, Redis, or feature flags via internal service catalogs
Popular IDP Tooling: Build vs Buy
Internal Developer Platforms aren’t typically one product, they’re a platform stack assembled by your platform team. Common building blocks include:
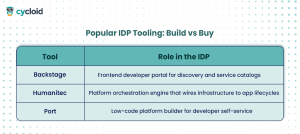
Many teams extend these tools with internal automation scripts, Terraform modules, GitHub Actions, and Kubernetes controllers. What matters is that the developer interface stays simple, while the platform logic stays composable.
The Payoff: Standardization Without the Bottleneck
IDPs help platform teams enforce golden paths and architectural standards, without making every change go through a ticket. They balance:
- Developer velocity (faster deploys, less waiting on ops)
- Infrastructure control (templates, policies, guardrails)
- Organizational scale (environments, pipelines, services that evolve as teams grow)
If you want developers to focus on shipping code, not on YAML, IAM, or infrastructure tickets, an IDP is the right abstraction.
Comparing CMP and IDP: Ownership, Users, and Operational Focus
Though Cloud Management Platforms (CMPs) and Internal Developer Platforms (IDPs) both sit in the platform engineering stack, they serve entirely different purposes and user bases. To choose the right abstraction layer, it’s critical to understand how these two approaches differ in ownership, integration, and day-to-day value.
Here’s a breakdown across four key dimensions:
1. Primary Users: Infra Teams vs. Application Developers
- CMPs are used by cloud operations and platform administrators who manage infrastructure access, quotas, and security policies.
- Example: A cloud engineer sets budget alerts or defines IAM roles for 50 AWS accounts.
- IDPs are built for application developers who need to deploy, test, and monitor their services without opening a ticket.
- Example: A backend engineer deploys a new service version using a Helm-based pipeline exposed through a developer portal.
Bottom line: CMPs are ops-first; IDPs are dev-first.
2. Ownership Model: Vendor-Managed vs. In-House Platforms
- CMPs are typically purchased from vendors (e.g., Morpheus, CloudBolt, Scalr) and maintained by the infra team. They’re “bought and configured.”
- IDPs are usually built internally using open-source tools and internal automation. Even if tools like Backstage or Humanitec are used, the workflows are tailored in-house.
CMPs come with governance baked in; IDPs require intentional design of developer workflows.
3. Integration Scope: Cloud APIs vs. App Lifecycle Tools
- CMPs integrate with cloud provider APIs, Terraform backends, and infrastructure orchestration systems.
- Examples: AWS Organizations, Azure Policy, GCP billing export, HashiCorp Vault
- IDPs plug into the application delivery toolchain, including Git repos, CI/CD pipelines, container registries, and deployment systems.
- Examples: GitHub Actions, ArgoCD, Helm charts, Kubernetes clusters
The integration point defines the abstraction: CMPs operate at the cloud account level; IDPs operate at the service lifecycle level.
4. Operational Focus: Governance vs. Developer Experience
CMPs Focus on Governance and Control
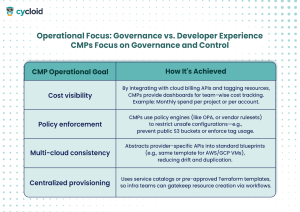
IDPs Focus on Developer Experience and Speed

A CMP helps your compliance team sleep at night. An IDP helps your developers ship before lunch.
TL;DR: Quick Comparison Table
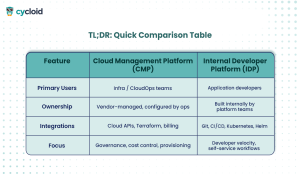
This side-by-side view should help clarify which abstraction layer is best aligned with your goals, and whether you might need both working in tandem.
Using Both in the Same Organization: Defining Clear Boundaries
For many large engineering organizations, choosing between a Cloud Management Platforms (CMP) and an Internal Developer Platform (IDP) isn’t an either/or decision. These platforms solve different problems for different personas, and when integrated cleanly, they can reinforce each other’s strengths.
But success depends on drawing clear boundaries between what each platform owns and exposes.
Cloud Management Platforms: Provisioning Secure, Compliant Cloud Infrastructure
Cloud Management Platforms form the infrastructure backbone, used to define, provision, and control cloud resources across multiple teams and environments. The CMP is where infrastructure teams:
- Manage cloud accounts, VPCs, IAM policies, quotas, and networking
- Apply budget controls and compliance policies globally
- Automate infrastructure creation with Terraform, but keep final approval or audit control
Everything at this layer is built with compliance, traceability, and repeatability in mind.
IDP: Offering a Curated, Developer-Friendly Subset
The Internal Developer Platform, by contrast, exposes only a safe, limited slice of infrastructure that’s needed for software delivery. Platform engineers create templates and workflows that:
- Reference pre-provisioned cloud resources (e.g., pre-approved Postgres clusters, base Kubernetes namespaces)
- Abstract complex infra actions into buttons, Git triggers, or pipelines
- Apply guardrails (naming, scaling, security) without giving raw access
For example, an IDP might let developers deploy to a sandbox namespace in EKS, but they never touch cluster-level IAM, network peering, or budget settings. Those stay controlled by the CMP layer.
Defining the Contract Between CMP and IDP
To make this dual-platform setup work smoothly, platform teams typically define explicit APIs and service contracts between the two layers:
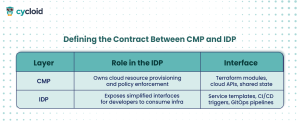
The IDP acts as a consumer of CMP-managed resources. The platform team ensures the right APIs, roles, and templates exist to make that interaction safe and repeatable.
What Goes Wrong Without Clear Separation
When responsibilities blur between CMP and IDP, things get messy fast:
- Duplicate workflows: Two ways to create environments, with different rules and tools
- Unmanaged sprawl: Developers accidentally bypass guardrails and create shadow infra
- Conflicting ownership: Devs file tickets with the wrong team; infra admins block feature teams unintentionally
- Loss of trust: Developers view the platform as inconsistent or unreliable
This is why mature orgs invest in designing the boundary as much as the platforms themselves. You don’t want two abstraction layers solving the same problem differently, you want each to complement the other.
Hands-On: Abstracting AWS Infrastructure with Terraform for Developer Self-Service
Not every organization starts with a full-fledged Internal Developer Platform, but that doesn’t mean you can’t begin delivering self-service experiences. If you’re using Terraform to manage infrastructure, you already have the foundation for exposing reusable abstractions to developers.
Let’s walk through how to create a developer-facing interface to deploy ECS services behind the scenes, using a Terraform module, a values.yaml input file, and a Git-based workflow.
Step 1: Create a Reusable Terraform Module
In a shared repo (e.g., infra-modules/ecs-service), define your ECS service module:
infra-modules/ecs-service/main.tf
| variable “service_name” {} variable “container_image” {} variable “cpu” { default = 256 } variable “memory” { default = 512 } variable “desired_count” { default = 1 } resource “aws_ecs_cluster” “main” { name = “${var.service_name}-cluster” } resource “aws_ecs_task_definition” “app” { family = var.service_name cpu = var.cpu memory = var.memory network_mode = “awsvpc” requires_compatibilities = [“FARGATE”] container_definitions = jsonencode([ { name = “app” image = var.container_image portMappings = [{ containerPort = 80 }] logConfiguration = { logDriver = “awslogs” options = { awslogs-group = “/ecs/${var.service_name}“ awslogs-region = var.region awslogs-stream-prefix = “ecs” } } } ]) } resource “aws_ecs_service” “app” { name = var.service_name cluster = aws_ecs_cluster.main.id task_definition = aws_ecs_task_definition.app.arn desired_count = var.desired_count launch_type = “FARGATE” network_configuration { subnets = var.subnets security_groups = var.security_groups assign_public_ip = true } load_balancer { target_group_arn = aws_lb_target_group.app.arn container_name = “app” container_port = 80 } depends_on = [aws_lb_listener.http] } |
You’ll also need to define the ALB, target group, and listener in the same module or in a core infra module.
Step 2: Wrap It with a values.yaml-Style Interface
Create a folder per app team with just a main.tf and a values file.
apps/my-service/values.auto.tfvars
| service_name = “my-service” container_image = “nginx:latest” cpu = 256 memory = 512 desired_count = 2 subnets = [“subnet-abc123”, “subnet-def456”] security_groups = [“sg-xyz789”] region = “us-east-1” |
apps/my-service/main.tf
| module “ecs_service” { source = “../../infra-modules/ecs-service” for_each = toset([“”]) service_name = var.service_name container_image = var.container_image cpu = var.cpu memory = var.memory desired_count = var.desired_count subnets = var.subnets security_groups = var.security_groups region = var.region } |
Now developers only edit values.auto.tfvars to deploy a service.
Step 3: Use GitHub Actions to Apply on Merge
.github/workflows/deploy.yml
| name: Deploy Service on: push: branches: – main jobs: terraform: name: Terraform Apply runs-on: ubuntu-latest steps: – name: Checkout code uses: actions/checkout@v3 – name: Set up Terraform uses: hashicorp/setup-terraform@v2 with: terraform_version: 1.5.0 – name: Terraform Init run: terraform init working-directory: apps/my-service – name: Terraform Plan run: terraform plan -var-file=values.auto.tfvars working-directory: apps/my-service – name: Terraform Apply run: terraform apply -auto-approve -var-file=values.auto.tfvars working-directory: apps/my-service |
Optional: Set up backend configuration and secret management using Terraform Cloud or S3 with remote state.
Step 4: Isolate Dev/Stage/Prod Using Workspaces
In your apps/my-service/backend.tf:
| terraform { backend “s3” { bucket = “my-terraform-state” key = “ecs/my-service/terraform.tfstate” region = “us-east-1” workspace_key_prefix = “env” } } |
Use separate workspaces:
| terraform workspace new dev terraform workspace new staging terraform workspace new prod |
Developers can deploy to an environment by switching workspaces:
| terraform workspace select staging terraform apply –var–file=values.auto.tfvars |
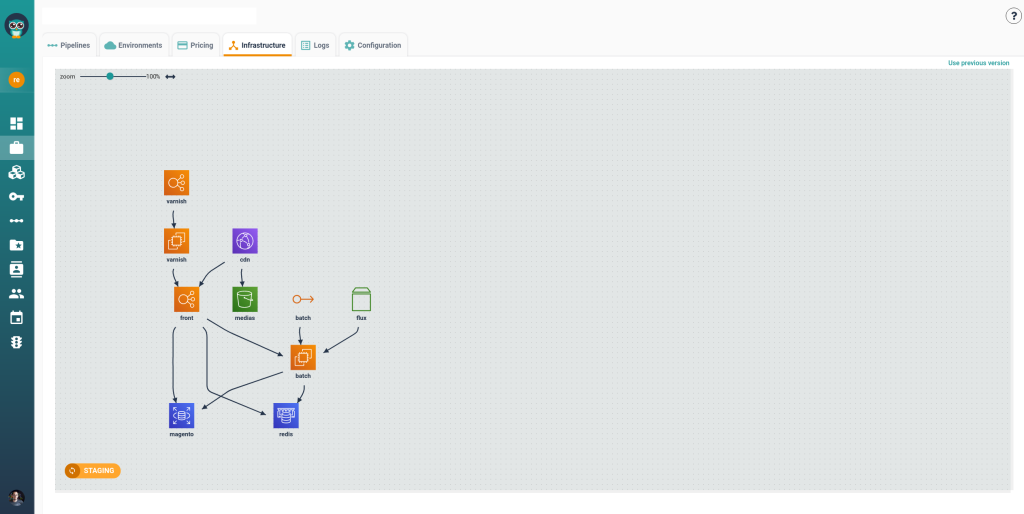
Here is the deployed version
Step 5: Add Minimal Documentation for Developers
README.md in the app folder:
| # Deploying My Service 1. Clone the repo. 2. Edit `values.auto.tfvars` with your image and scaling config. 3. Push changes to `main` to trigger deployment. 4. View logs in CloudWatch: `/ecs/my-service`. Contact the platform team for subnet/security group IDs. |
Why This Works, Even Without a Full IDP
This pattern, Terraform modules + YAML interface + CI pipelines, gives you:
- Reusability across services and teams
- Guardrails without blocking velocity
- Minimal exposure to raw infrastructure
- A foundation to later scale into a full IDP using tools like Backstage or Port
You’re not building a platform from scratch, you’re abstracting what you already use.
How Cycloid Solves Both
Most organizations manage two layers: a Cloud Management Platforms (CMP) for infrastructure teams and an Internal Developer Platform (IDP) for app developers. This works, but it can be heavy. Teams need to build and maintain separate tools, enforce handoffs, and continuously manage integration boundaries.
Cycloid offers a streamlined alternative: a single platform that delivers both CMP-level control and IDP-level usability without splitting your stack.
Here’s how it helps:
1. A Unified Developer Portal for Git-Based Self-Service
Cycloid provides a developer-friendly portal that abstracts infrastructure complexity behind Git-driven workflows:
- Developers use pre-approved templates (e.g., ECS services, databases) to provision and deploy.
- Changes are committed to Git and run through a CI/CD pipeline, promoting version control and review.
- No need to learn Terraform, cloud consoles, or Kubernetes details, just YAML inputs and Git pushes.
2. Native Terraform and Cloud Governance Integration
Unlike traditional IDPs that require bolting on a CMP, Cycloid integrates core CMP features directly:
- Terraform module orchestration: Write once, expose as reusable templates.
- Cloud account governance: Centralize roles, budgets, and IAM across AWS, Azure, or GCP.
- Cost visibility: Built-in dashboards give platform teams a real-time view of usage and spend.
This dual focus enables consistent compliance and cost control without compromising developer agility.
3. Controlled Exposure Without Compromising Security
With Cycloid, platform teams define what’s available to developers, and what isn’t:
- Developers get access to curated environments and modules with scoped permissions.
- Platform teams keep control over secrets, cloud credentials, network boundaries, and Terraform state.
- Policies can be enforced centrally (e.g., tagging, quotas, regions) while still supporting team-specific use cases.
Conclusion
Choosing the right abstraction layer, CMP or IDP, is not just a tooling decision. It’s about aligning infrastructure operations with developer experience.
- CMPs shine when you need control: multi-cloud governance, compliance, and cost optimization.
- IDPs excel when you need speed: streamlined workflows, self-service deployment, and reduced ticket ops.
In reality, most mature organizations need both layers, but maintaining two stacks is complex.
Cycloid offers a middle path: a unified approach that empowers developers without losing governance. Whether you’re scaling an enterprise platform team or just starting to modernize your DevOps processes, Cycloid brings structure without overhead.
FAQs
Q: Can I use Cycloid without migrating my infrastructure?
Yes. Cycloid integrates with existing Terraform modules and CI/CD pipelines. You don’t need to rewrite or replatform your infrastructure.
Q: How is Cycloid different from Backstage or Humanitec?
Backstage is a developer portal framework, great for UI, but it doesn’t handle infra orchestration. Humanitec is IDP-focused but lacks native multi cloud management platform features. Cycloid combines both: portal + infra provisioning + cost and governance.
Q: Is Cycloid only for large enterprises?
No. It’s used by organizations of all sizes, from startups standardizing infrastructure early to enterprises unifying sprawling DevOps toolchains.
Q: Does Cycloid work with multi-cloud setups?
Absolutely. Cycloid supports AWS, Azure, and GCP natively, making it easier to centralize governance and expose consistent deployment patterns across clouds.
Q: What if I already use Terraform Cloud or GitHub Actions?
Cycloid doesn’t replace them, it wraps around them. You can continue using your existing CI/CD systems and backend providers while gaining a higher-level interface for developers.