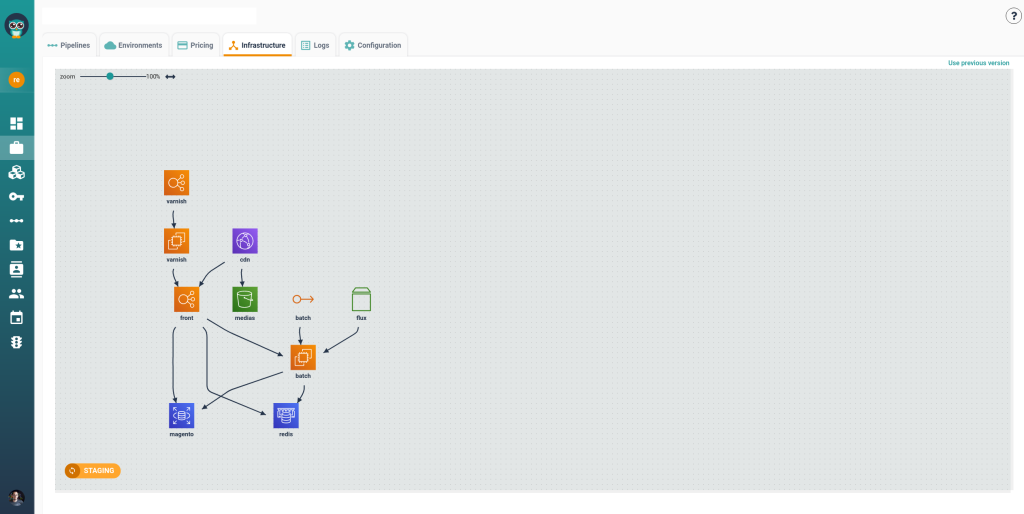
TL;DR
- Hybrid cloud operations collapse into chaos when tenant rules live in tribal knowledge rather than the platform itself.
- Adding more engineers to manage multi-cloud handoffs scales linearly; the only way to protect margins is to replace manual “inbox triage” with platform-enforced governance.
- When you embed limits and compliance directly into templates (Stacks) and pipelines (InfraPolicies), you don’t need human approval to ensure safety.
- You can allow tenants to deploy their own infrastructure, even in regulated environments, if the platform automatically rejects non-compliant requests before they happen.
- Moving from “ticket-based approvals” to “policy-as-code” turns a 4-hour wait time into a 4-second feedback loop, freeing engineers to operate instead of coordinate.
- Cycloid solves this by abstracting the underlying cloud complexity:
- Stacks provide a single interface to deploy across any provider (Terraform/Helm/Ansible).
- InfraPolicies enforce one set of governance rules (OPA) that works on-prem and in the cloud.
- GreenOps unifies cost visibility, normalizing spend data across disparate billing models.
Introduction
A mid-sized MSP running fifteen enterprise customers across bare metal, on-prem VMware, AWS, OpenShift, and Azure does not fail because of technology choice. It fails because traditional change management processes turn every network change, environment request, cost question, or compliance check into a ticket in platforms like ServiceNow, forcing manual coordination across disconnected tools, teams, and calendars.
Omdia’s October 2025 analysis reports that MSP operating margins are under renewed pressure as rising labor costs collide with increasingly complex hybrid estates. Service providers are finding that traditional “people-first” support models cannot scale with the double-digit growth in multi-cloud management demands. More platforms did not reduce the load. They multiplied the handoffs.
Spend time in r/msp or r/sysadmin and the pattern is familiar. Engineers describe hybrid cloud work as inbox triage, where tenant context lives in tribal knowledge, approvals depend on who is online, and no system has a complete view of what a customer is allowed to run. The cloud did not slow teams down. The absence of a shared control plane did.
The operational failure isn’t caused by the hybrid architecture itself, but by the manual governance model used to manage it. This article breaks down how MSPs structure hybrid cloud platforms to enforce tenant isolation, apply governance once, and offer self-service that does not turn operations into a ticket factory.
Why Hybrid Cloud Turns MSPs Into Ticket Factories
It is not the volume of infrastructure that breaks MSP operations; it is the overwhelming density of tenant-specific rules, security constraints, and environment variables that engineers must manually verify. When a platform cannot distinguish between a high-compliance banking tenant and a low-priority test environment, every decision falls back to an engineer.
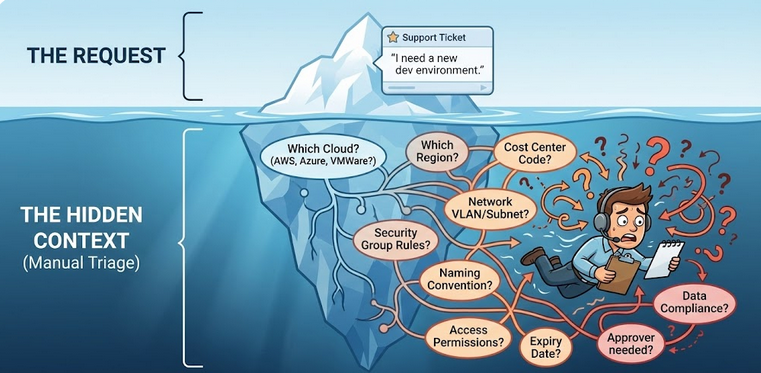
Here is how that gap creates the “Ticket Factory”:
Hybrid Environments Multiply Context, Not Just Infrastructure
Hybrid cloud environments span on-prem clusters, multiple public clouds, and shared delivery tooling. Each tenant arrives with its own constraints around regions, security controls, and cost limits. Without a common operating model, every change request becomes custom work that must be interpreted before it can be executed.
The platform does not understand tenant intent. Engineers do. That gap is where tickets appear.
But where does that intent live if not in the platform? It hides in the team’s memory.
Tenant Fragmentation Lives in People’s Heads
Fragmentation is often functional, not just historical. A single customer might rely on Google Cloud for data workloads (like Dataproc) while mandating Azure for Active Directory integration. This means “Customer A” exists in fragments: their identity rules live in one cloud, while their compute constraints live in another.
Engineers are forced to mentally stitch these disparate environments together because no single tool has the full picture.
Tool Sprawl Breaks Ownership and Visibility
Sprawl isn’t just about having too many tools; it is about the blindness between them. Consider a legacy service running on-premise that needs to connect to a data workload on GCP.
To debug a connectivity issue, an engineer has to toggle between physical network logs and the Google Cloud Console, neither of which acknowledges the other exists. Ownership is lost in the gap: the on-prem team sees traffic leave, and the cloud team sees it arrive, but no single tool tracks the dependency. Because no platform provides a full picture, engineers fall back to tickets to manually correlate systems that were never designed to agree.
Human Approval Loops Replace Platform Enforcement
Routine actions, like spinning up a new Kubernetes cluster, opening a firewall port for a database, or scaling an instance, rely on human approval because rules are not enforced by the platform itself.
Tickets feel safe because they slow things down, but that safety comes at a cost. Lead times increase, margins shrink, and engineers spend more time coordinating than operating.
What “Multi-Tenant Hybrid Cloud” Actually Means for an MSP
To fix the ticket factory, we first need to agree on what the “factory floor” actually looks like. It is bigger than most MSPs admit.
The Real Surface Area MSPs Are Responsible For
A multi-tenant hybrid cloud is not just about running multiple accounts. MSPs operate a shared surface area that spans on-prem and public cloud infrastructure, shared pipelines with tenant-specific rules, identity and access boundaries, and cost and usage visibility tied to each customer.
On top of this, compliance expectations vary by tenant and often by workload. The platform must reflect these differences explicitly, or they surface as manual checks later.
But recognizing this surface area is only half the battle. The common trap is trying to manage this complexity with paperwork instead of software.
The Common Mistake: Treating Tenants as a Process Problem
Many teams treat tenant separation as documentation and process. Runbooks describe what is allowed. Naming conventions signal ownership. Tickets enforce exceptions. This works when the change volume is low and collapses as soon as delivery speed increases.
In this model, the platform has no understanding of tenant boundaries. Enforcement depends on people remembering and applying rules correctly.
So, if a process fails, how do we enforce boundaries technically?
From Manual Separation to Enforced Boundaries
Earlier models relied on manual separation enforced by spreadsheets, approval steps, and experience. Isolation existed, but it lived outside the system. Audits depended on explanations rather than evidence.
In current hybrid estates, tenant isolation must be enforced by infrastructure, policy, and runtime boundaries. The platform needs to know who owns a workload, where it can run, and what limits apply before anything is provisioned. When these boundaries are explicit, self-service becomes possible without reopening the ticket queue.
Once you decide to enforce boundaries technically, you have to choose an architecture. Most MSPs fall into one of three patterns.
Tenant Isolation Models MSPs Use in Hybrid Cloud
Not all isolation is created equal. The right choice depends on how much overhead you are willing to trade for safety.
1. Model One: Hard-Isolated Environments
In this model, each tenant runs in separate cloud accounts, clusters, and pipelines. The blast radius is clear and audits are easier to explain.
The Trade-off:
The cost shows up quickly. Every tenant repeats the same setup work. Onboarding is slow. Shared improvements take time to propagate. Isolation is strong, but operational overhead grows linearly with customer count.
If hard isolation is too expensive, many MSPs swing to the opposite extreme.
2. Model Two: Shared Platform With Logical Isolation
Here, tenants run on a shared control plane with enforced boundaries around identity, networking, and resource usage. Pipelines, templates, and tooling are reused across customers.
The Trade-off:
This model improves consistency and speeds up onboarding. It depends on strong identity controls, tagging discipline, and policy enforcement. When these controls are weak, tenant trust erodes fast.
Ideally, we want the best of both worlds. That leads us to the hybrid approach.
3. Model Three: Mixed Isolation by Workload Class
Sensitive or regulated workloads run in isolated environments, while standard services share infrastructure under strict limits. This balances cost and risk for MSPs serving diverse customers.
The Trade-off:
The risk is classification drift. If a workload is misclassified, isolation breaks. MSPs using this model rely on the platform to apply boundaries automatically rather than on engineers choosing the correct path every time.
Regardless of the model you pick, isolation is useless if you still need a human to unlock the door for every change. This brings us to the real bottleneck: Governance.
Governance Without Tickets in a Hybrid MSP Model
Isolation defines where things run. Governance defines what is allowed to run. Traditionally, this is where the speed stops.
Why Ticket-Driven Governance Fails at MSP Scale
In many MSP environments, governance still runs through tickets because rules live outside the platform. A request arrives, an engineer checks a document, asks clarifying questions, and approves or rejects based on experience. The ticket becomes the enforcement layer.
The Consequence:
This model collapses in hybrid cloud setups. As tenants increase and environments diverge, human reviews turn governance into a queue. Context shifts between teams. The same change is handled differently depending on who reviews it. Safety comes from delay, not from control.
The solution is to stop asking people to be the firewall.
How Embedded Governance Changes the Operating Model
This is where InfraPolicies become important. By embedding governance into templates and pipelines. Instead of asking for approval, a request is validated against constraints that already exist in the platform. Enforcement is consistent because it is executed by code, not interpreted by individuals.
The platform becomes aware of tenant boundaries, allowed regions, network rules, and cost limits. Decisions happen before resources exist, not after problems appear.
What “Shifting Governance Left” Looks Like in Practice
MSPs move governance left by applying limits at provisioning time. Region and cloud choices are restricted during creation rather than reviewed after deployment. Network access and identity boundaries are applied by default. Cost and usage limits are enforced per tenant before spend accumulates.
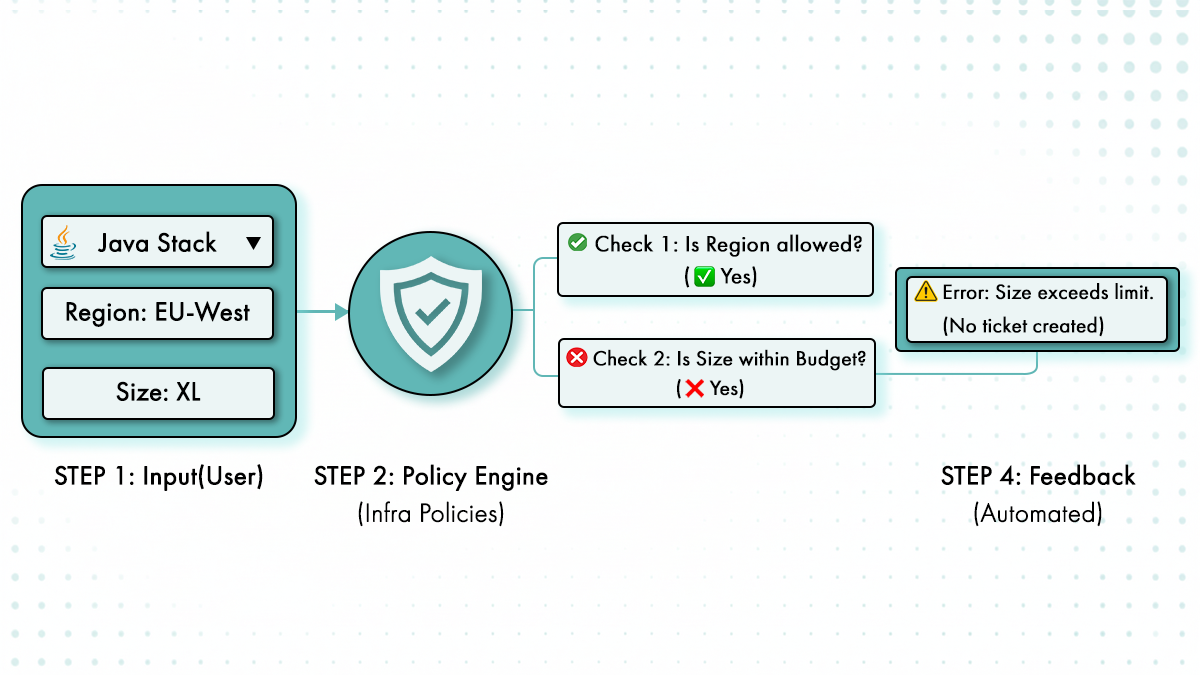
Outcome
For engineers and tenant teams, the outcome is fewer back-and-forths and clearer expectations. The rules are visible because the platform enforces them every time. Governance stops being a ticket queue and becomes part of the delivery flow.
When governance is automated, the bottleneck moves. Now the question isn’t “Can I do this?”, it is “How do I do this without waiting?”
Self-Service That Respects Tenant Boundaries
True self-service is impossible if you don’t trust the user. But if the platform enforces the rules, you don’t need to trust them.
The Manual Work MSP Engineers Are Still Doing
In many MSP setups, self-service exists in name only. Engineers still clone Terraform repositories, rename resources to match tenant conventions, and cross-check limits against documentation before making a change. Cost exposure is reviewed after the fact, often by someone outside the delivery flow.
Each of these steps adds friction because none of them are enforced by the platform. They rely on discipline and experience. When something is unclear, the fallback is chat messages or tickets asking for confirmation. The request slows down, not because it is complex, but because the system cannot answer basic questions about tenant limits.
What Self-Service Looks Like When Boundaries Are Enforced
Real self-service starts when tenant boundaries are embedded in the request itself. Instead of cloning and editing infrastructure code, teams work from tenant-scoped templates. Inputs are limited to what a tenant is allowed to change. Everything else is fixed by policy.
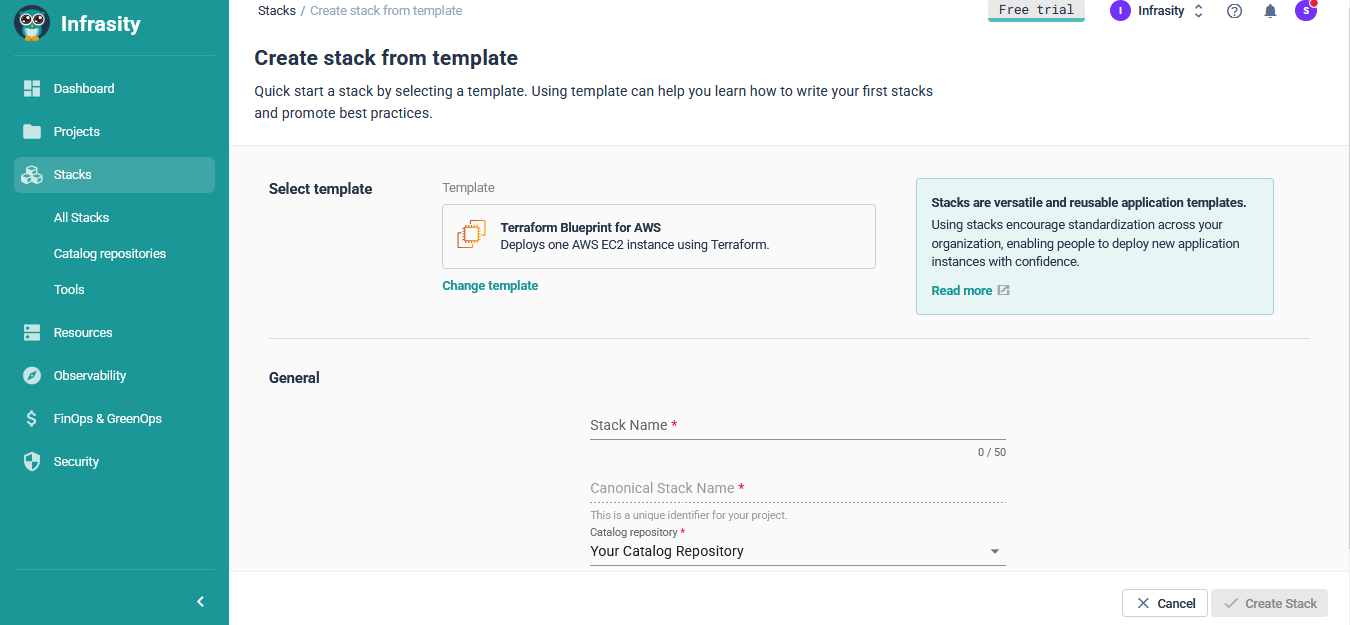
Engineers don’t start from a blank slate; they start from a defined Stack. This form limits inputs to only what the tenant is allowed to change, ensuring compliance before a single line of code is written.
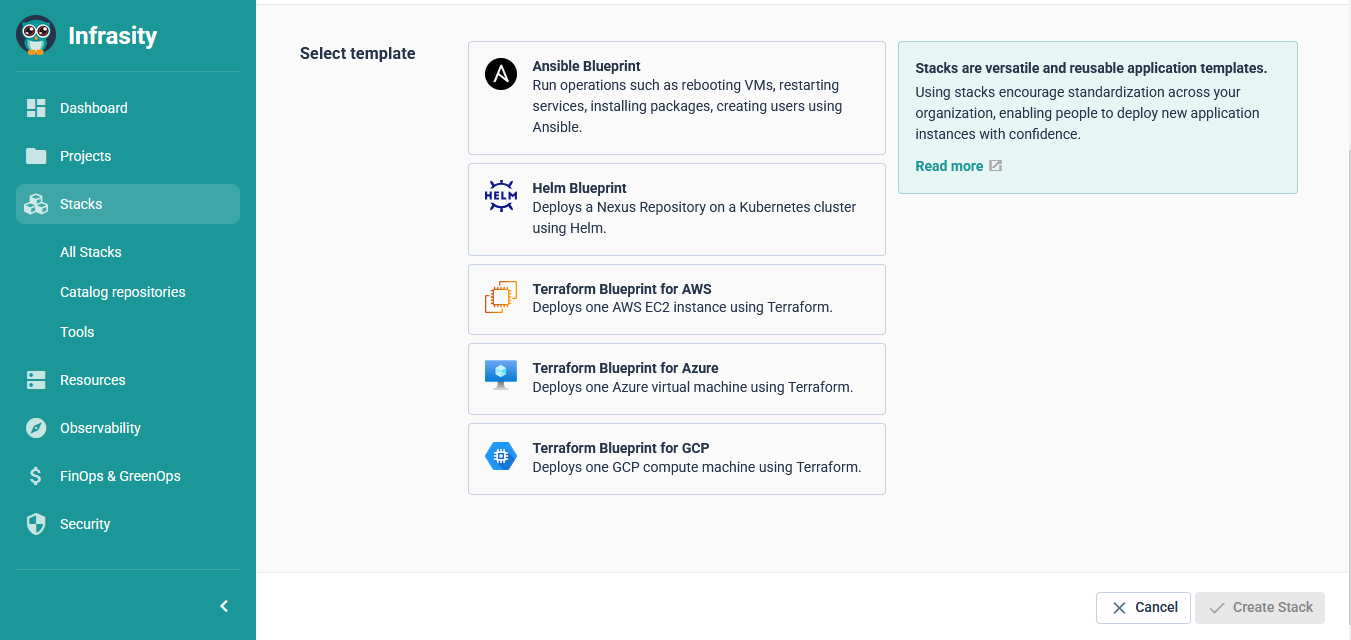
One can select from a unified catalog in Cycloid where an Azure identity service sits right next to a Google Cloud data workload, all governed by the same rules
Region choices are constrained. Environment types are predefined. Cost and capacity limits are applied automatically. When a request violates a rule, feedback is immediate and specific. There is no waiting for an approval because the platform already enforces the boundary.
This approach removes manual review without removing control. Engineers spend less time validating intent and more time operating the platform.
Example: Tenant-Scoped Environment Request
File: tenant-environment.yaml
| tenant_id: acme-finance environment: production region: eu-west-1 limits: monthly_budget_usd: 8000 max_nodes: 12 network: exposure: internal allowed_ingress: – vpn compliance: data_classification: sensitive |
What happens when the request violates a rule: Instead of a ticket sitting in a queue for 4 hours, the engineer gets instant feedback in the terminal:
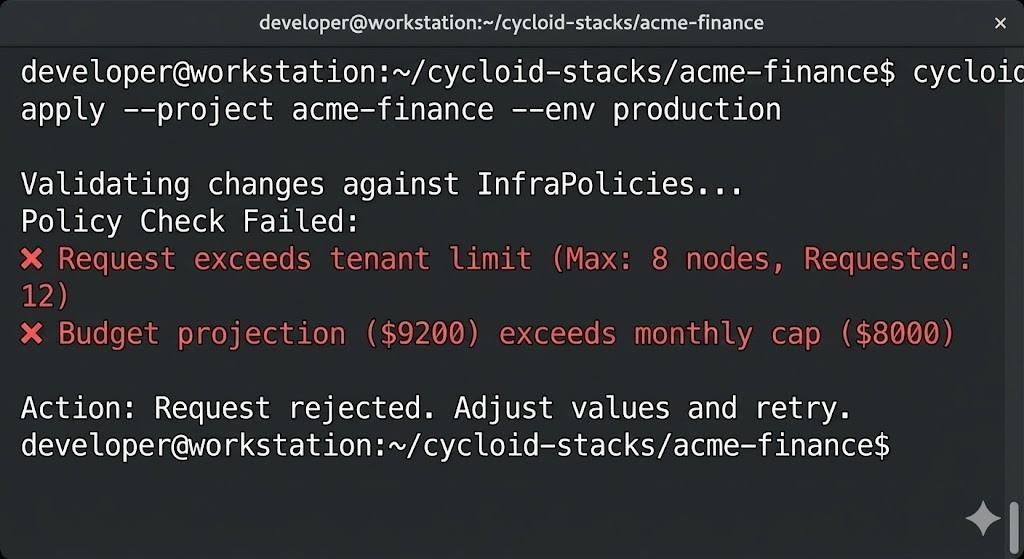
This is the difference between a platform and a ticket. The rejection is instant, impersonal, and strictly enforced.
How MSPs Measure Success Beyond Ticket Volume
If your dashboard is green because you closed 500 tickets this week, you might be failing.
Metrics That Reflect Platform Health, Not Activity
Counting closed tickets says nothing about whether a hybrid cloud platform is working. MSP platform teams track metrics that reflect flow, predictability, and control.
- Change lead time per tenant: Shows how quickly a request moves from intent to deployment. A drop here usually correlates with boundaries enforced by the platform rather than reviewed by people.
- Manual approvals per deployment: Highlights how much governance still relies on human intervention. As this number approaches zero, ticket load falls without sacrificing safety.
But speed isn’t everything. You also need to measure control.
Measuring Onboarding, Cost, and Policy Behavior
- Tenant onboarding time: Exposes how repeatable the platform really is. When new customers require weeks of setup, isolation and governance are still handcrafted.
- Cost variance against tenant budgets: Often tracked via GreenOps dashboards, this shows whether limits are enforced or only observed. Low variance means budgets are part of provisioning, not reporting.
- Policy violations caught before deployment: Indicate how much risk is absorbed by the platform instead of leaking into production. This metric replaces post-incident reviews with predictable enforcement.
Together, these signals replace “number of tickets closed” with measures that show whether the MSP is operating a platform or running a help desk.
This sounds great, but how do you get there without pausing operations for six months?
A Practical Adoption Path for MSPs
Step 1: Start by Making Tenant Boundaries Explicit
Most MSPs already have tenant boundaries, but they live in diagrams, naming rules, or ticket templates. The first step is to make those boundaries visible to the platform. Identify which services are shared, which are tenant-specific, and which workloads require isolation. This work feels slow, but it removes ambiguity that later shows up as approvals and rework.
At this stage, nothing is blocked. The goal is clarity, not enforcement.
Step 2: Standardize a Small Set of Tenant-Ready Stacks
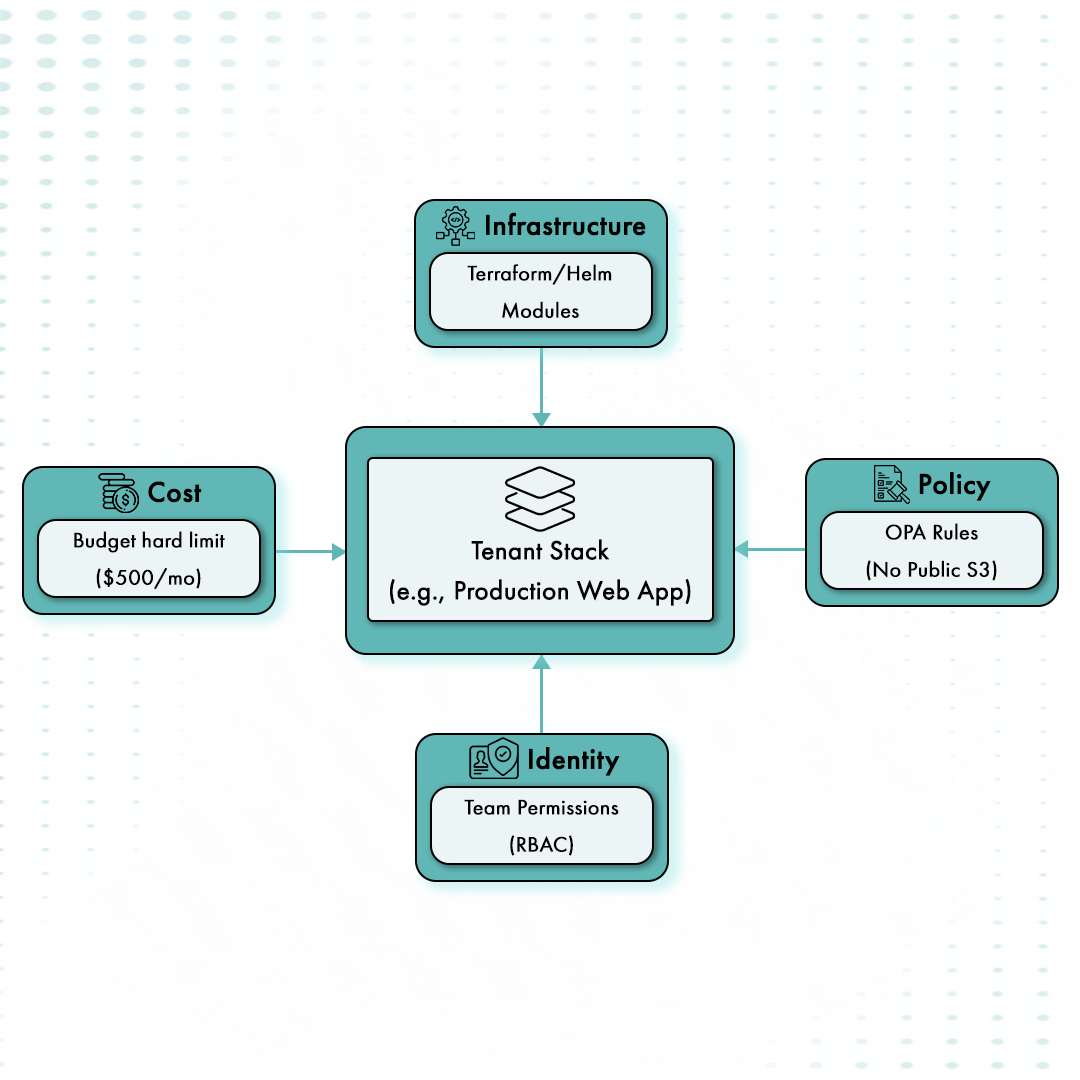
Once boundaries are clear, MSPs reduce variation by defining a small number of tenant-ready stacks. These stacks encode what a “normal” environment looks like for common use cases, including network shape, identity boundaries, and cost limits.
The mistake is trying to cover every edge case up front. Teams that succeed start with two or three patterns they can repeat across customers. Anything outside those patterns is treated as an exception, not a new default.
Step 3: Introduce Visibility Before Enforcement
Before rules start rejecting requests, teams expose them. Developers and operators see which regions are allowed, what budgets apply, and where policy limits sit. Violations are flagged but not blocked.
This phase builds trust. Teams learn how the platform thinks, and platform teams validate that rules match reality. When enforcement begins later, it feels predictable rather than abrupt.
Step 4: Gradually Remove Ticket-Based Approvals
As rules move into templates and policies, ticket-based approvals lose their purpose. Access requests, environment creation, and routine changes no longer need human review because the platform already enforces tenant limits.
Approvals disappear in stages. First for low-risk changes, then for core workflows. The ticket queue shrinks without a hard cutover, and engineers regain time without losing control.
Step 5: Handle Exceptions Without Breaking Flow
Exceptions never disappear. What changes is how they are handled. Instead of reopening manual reviews for everything, exceptions are documented as explicit overrides with scope and expiry.
This keeps flow intact. The platform remains the source of truth, and exceptions do not silently become new norms.
Closing Takeaways
| Dimension | Ticket-Driven Hybrid Operations | Platform-Driven Hybrid Operations |
| Tenant Isolation | Enforced through process | Enforced by infrastructure and policy |
| Governance | Manual reviews and approvals | Rules applied on every change |
| Developer and Ops Flow | Interrupt-driven | Predictable self-service |
| Cost Control | Reviewed after spend | Limits applied before provisioning |
| MSP Scalability | Linear headcount growth | Repeatable patterns across tenants |
Conclusion
Moving away from a ticket-heavy workflow is about sustainability. As hybrid environments expand, relying on manual reviews creates bottlenecks that more headcount cannot fix. By embedding rules directly into the platform, MSPs gain consistency and speed without sacrificing control. The goal is to let the system handle the boundaries so engineers can focus on the work that actually adds value to the tenant.
Ready to see how this works in practice? Cycloid’s engineering team can walk you through setting up Stacks and InfraPolicies to match your specific governance needs. Book a technical demo to explore the platform.
FAQs
-
What makes hybrid cloud harder for MSPs than single-cloud setups?
Hybrid cloud combines on-prem infrastructure with multiple public clouds, each with different control models, billing mechanics, and failure modes. For MSPs, the challenge is not connectivity. It is operating consistent tenant boundaries across environments that were never designed to work together. Without a shared control plane, every difference becomes a manual check.
-
Why is the hybrid multicloud approach more beneficial than a traditional public cloud only approach?
A hybrid multicloud approach delivers the agility and scalability of the public cloud with the enhanced sovereignty and control over workloads and data you get with private clouds and on-premises infrastructure.
-
How do MSPs enforce tenant isolation without duplicating everything?
MSPs avoid full duplication by enforcing logical isolation on a shared platform. Identity boundaries, network segmentation, and resource limits are applied by policy rather than by separate environments. Sensitive workloads can still run in isolated stacks, but common services and pipelines are reused under strict controls.
-
What role does a cloud management platform play in MSP hybrid setups?
A cloud management platform gives MSPs a single place to define tenant boundaries, enforce governance, and expose self-service. It connects infrastructure, pipelines, and cost controls so that tenant intent is enforced automatically. Without it, hybrid cloud operations fall back to tickets and tribal knowledge.